It can be a real nightmare if someone hacks and takes control of your email account as it may contain confidential information like bank logins, credit card details and other sensitive data. If you are one such Internet user whose email account has been compromised, then this post will surely help you out. In this post you will find the possible ways and procedures to get back your hacked email account.
For Gmail:
It can be a big disaster if your Gmail account has been compromised as it may be associated with several services like Blogger, Analytics, Adwords, Adsense, Orkut etc. Losing access to your Gmail account means losing access to all the services associated it with too. Here is a list of possible recovery actions that you can try.
Step -1: Try resetting your password since it is the easiest way to get your account back in action. In this process Google may ask you to answer the secret question or may send the password reset details to the secondary email address associated with your compromised account. You can reset you password from the following link
Gmail Password Reset Link
If you cannot find success from the Step-1 then proceed to Step-2.
Step-2: Many times the hacker will change the secret question and secondary email address right after the account is compromised. This is the reason for the Password Reset process to fail. If this is the case then you need to contact the Gmail support team by filling out the account recovery form. This form will ask you to fill out several questions like
1. Email addresses of up to five frequently emailed contacts
2. Names of any 4 Labels that you may have created in your account
3. List of other services associated with your compromised account
4. Your last successful login date
5. Account created date
6. Last password that you remember and many more…
You need to fill out this form as much accurately as possible. It is obvious to forget the dates of last login, account creation and similar terms. However you need to figure out the closest possible date/answers and fill out this form. This is your last chance! The more accurate the information filled out in the recovery form, the more the chances of getting your account back. You may reach the account recovery page form the following link
Account Recovery Form
For Yahoo and Hotmail:
Unfortunately for Yahoo/Hotmail there is no second option like filling out the form or contacting the support team. All you need to do is either answer the secret questions that you have setup or reset the password using the secondary email option.
To initiate the password reset process just click on the Forgot password link in your login page and proceed as per the screen instructions.
I hope this post will help you recover the lost account. I highly recommend that you also read my post on How to protect your email account from being hacked and Tips to find unauthorized activity on your Gmail account so that you always stay protected
Sunday, May 30, 2010
Saturday, May 22, 2010
Top reasons Why PC’s Crash – Curing Blue Screen of Death
“Fatal error: the system has become unstable or is busy," it says. "Enter to return to Windows or press Control-Alt-Delete to restart your computer. If you do this you will lose any unsaved information in all open applications."
You have just been struck by the Blue Screen of Death.
Anyone who uses Microsoft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening?
Lets get down on it…
Hardware conflict
The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device.
For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself.
If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route:
* Start-Settings-Control Panel-System-Device Manager.
Often if a device has a problem a yellow '!' appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it.
Sometimes a device might share an IRQ with something described as 'IRQ holder for PCI steering'. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it.
Sometimes you may have to find more recent drivers on the internet to make the device function properly. A good resource is www.driverguide.com. If the device is a soundcard, or a modem, it can often be fixed by moving it to a different slot on the motherboard (be careful about opening your computer, as you may void the warranty).
When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity.
To be fair to Microsoft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs.
Bad Ram
Ram (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing.
But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked.
One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can make it more stable. Another way to troubleshoot a suspected Ram problem is to rearrange the Ram chips on the motherboard, or take some of them out. Then try to repeat the circumstances that caused the crash. When handling Ram try not to touch the gold connections, as they can be easily damaged.
Parity error messages also refer to Ram. Modern Ram chips are either parity (ECC) or non parity (non-ECC). It is best not to mix the two types, as this can be a cause of trouble.
EMM386 error messages refer to memory problems but may not be connected to bad Ram. This may be due to free memory problems often linked to old Dos-based programs.
BIOS settings
Every motherboard is supplied with a range of chipset settings that are decided in the factory. A common way to access these settings is to press the F2 or delete button during the first few seconds of a boot-up.
Once inside the BIOS, great care should be taken. It is a good idea to write down on a piece of paper all the settings that appear on the screen. That way, if you change something and the computer becomes more unstable, you will know what settings to revert to.
A common BIOS error concerns the CAS latency. This refers to the Ram. Older EDO (extended data out) Ram has a CAS latency of 3. Newer SDRam has a CAS latency of 2. Setting the wrong figure can cause the Ram to lock up and freeze the computer's display.
Microsoft Windows is better at allocating IRQ numbers than any BIOS. If possible set the IRQ numbers to Auto in the BIOS. This will allow Windows to allocate the IRQ numbers (make sure the BIOS setting for Plug and Play OS is switched to 'yes' to allow Windows to do this.).
Hard disk drives
After a few weeks, the information on a hard disk drive starts to become piecemeal or fragmented. It is a good idea to defragment the hard disk every week or so, to prevent the disk from causing a screen freeze. Go to
* Start-Programs-Accessories-System Tools-Disk Defragmenter
This will start the procedure. You will be unable to write data to the hard drive (to save it) while the disk is defragmenting, so it is a good idea to schedule the procedure for a period of inactivity using the Task Scheduler.
The Task Scheduler should be one of the small icons on the bottom right of the Windows opening page (the desktop).
Some lockups and screen freezes caused by hard disk problems can be solved by reducing the read-ahead optimisation. This can be adjusted by going to
* Start-Settings-Control Panel-System Icon-Performance-File System-Hard Disk.
Hard disks will slow down and crash if they are too full. Do some housekeeping on your hard drive every few months and free some space on it. Open the Windows folder on the C drive and find the Temporary Internet Files folder. Deleting the contents (not the folder) can free a lot of space.
Empty the Recycle Bin every week to free more space. Hard disk drives should be scanned every week for errors or bad sectors. Go to
* Start-Programs-Accessories-System Tools-ScanDisk
Otherwise assign the Task Scheduler to perform this operation at night when the computer is not in use.
Fatal OE exceptions and VXD errors
Fatal OE exception errors and VXD errors are often caused by video card problems.These can often be resolved easily by reducing the resolution of the video display. Go to
* Start-Settings-Control Panel-Display-Settings
Here you should slide the screen area bar to the left. Take a look at the color settings on the left of that window. For most desktops, high color 16-bit depth is adequate.
If the screen freezes or you experience system lockups it might be due to the video card. Make sure it does not have a hardware conflict. Go to
* Start-Settings-Control Panel-System-Device Manager
Here, select the + beside Display Adapter. A line of text describing your video card should appear. Select it (make it blue) and press properties. Then select Resources and select each line in the window. Look for a message that says No Conflicts.
If you have video card hardware conflict, you will see it here. Be careful at this point and make a note of everything you do in case you make things worse.
The way to resolve a hardware conflict is to uncheck the Use Automatic Settings box and hit the Change Settings button. You are searching for a setting that will display a No Conflicts message.
Another useful way to resolve video problems is to go to
* Start-Settings-Control Panel-System-Performance-Graphics
Here you should move the Hardware Acceleration slider to the left. As ever, the most common cause of problems relating to graphics cards is old or faulty drivers (a driver is a small piece of software used by a computer to communicate with a device).
Look up your video card's manufacturer on the internet and search for the most recent drivers for it.
Viruses
Often the first sign of a virus infection is instability. Some viruses erase the boot sector of a hard drive, making it impossible to start. This is why it is a good idea to create a Windows start-up disk. Go to
* Start-Settings-Control Panel-Add/Remove Programs
Here, look for the Start Up Disk tab. Virus protection requires constant vigilance.
A virus scanner requires a list of virus signatures in order to be able to identify viruses. These signatures are stored in a DAT file. DAT files should be updated weekly from the website of your antivirus software manufacturer.
An excellent antivirus program is McAfee Virus Scan by Network Associates ( www.nai.com). Another is Norton Antivirus 2000, made by Symantec ( www.symantec.com).
Printers
The action of sending a document to print creates a bigger file, often called a postscript file.
Printers have only a small amount of memory, called a buffer. This can be easily overloaded. Printing a document also uses a considerable amount of CPU power. This will also slow down the computer's performance.
If the printer is trying to print unusual characters, these might not be recognized, and can crash the computer. Sometimes printers will not recover from a crash because of confusion in the buffer. A good way to clear the buffer is to unplug the printer for ten seconds. Booting up from a powerless state, also called a cold boot, will restore the printer's default settings and you may be able to carry on.
Software
A common cause of computer crash is faulty or badly-installed software. Often the problem can be cured by uninstalling the software and then reinstalling it. Use Norton Uninstall or Uninstall Shield to remove an application from your system properly. This will also remove references to the program in the System Registry and leaves the way clear for a completely fresh copy.
The System Registry can be corrupted by old references to obsolete software that you thought was uninstalled. Use Registry Cleaner to clean up the System Registry and remove obsolete entries.
Often a Windows problem can be resolved by entering Safe Mode. This can be done during start-up. When you see the message "Starting Windows" press F4. This should take you into Safe Mode.
Safe Mode loads a minimum of drivers. It allows you to find and fix problems that prevent Windows from loading properly.
Sometimes installing Windows is difficult because of unsuitable BIOS settings. If you keep getting SUWIN error messages (Windows setup) during the Windows installation, then try entering the BIOS and disabling the CPU internal cache. Try to disable the Level 2 (L2) cache if that doesn't work.
Remember to restore all the BIOS settings back to their former settings following installation.
Overheating
Central processing units (CPUs) are usually equipped with fans to keep them cool. If the fan fails or if the CPU gets old it may start to overheat and generate a particular kind of error called a kernel error. This is a common problem in chips that have been overclocked to operate at higher speeds than they are supposed to.
One remedy is to get a bigger better fan and install it on top of the CPU. Specialist cooling fans/heatsinks are available from www.computernerd.com or www.coolit.com
CPU problems can often be fixed by disabling the CPU internal cache in the BIOS. This will make the machine run more slowly, but it should also be more stable.
Power supply problems
With all the new construction going on around the country the steady supply of electricity has become disrupted. A power surge or spike can crash a computer as easily as a power cut.
If this has become a nuisance for you then consider buying a uninterrupted power supply (UPS). This will give you a clean power supply when there is electricity, and it will give you a few minutes to perform a controlled shutdown in case of a power cut.
It is a good investment if your data are critical, because a power cut will cause any unsaved data to be lost.
I hope now you will be able to rectify your problems. keep reading and learning.
You have just been struck by the Blue Screen of Death.
Anyone who uses Microsoft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening?
Lets get down on it…
Hardware conflict
The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device.
For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself.
If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route:
* Start-Settings-Control Panel-System-Device Manager.
Often if a device has a problem a yellow '!' appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it.
Sometimes a device might share an IRQ with something described as 'IRQ holder for PCI steering'. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it.
Sometimes you may have to find more recent drivers on the internet to make the device function properly. A good resource is www.driverguide.com. If the device is a soundcard, or a modem, it can often be fixed by moving it to a different slot on the motherboard (be careful about opening your computer, as you may void the warranty).
When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity.
To be fair to Microsoft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs.
Bad Ram
Ram (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing.
But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked.
One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can make it more stable. Another way to troubleshoot a suspected Ram problem is to rearrange the Ram chips on the motherboard, or take some of them out. Then try to repeat the circumstances that caused the crash. When handling Ram try not to touch the gold connections, as they can be easily damaged.
Parity error messages also refer to Ram. Modern Ram chips are either parity (ECC) or non parity (non-ECC). It is best not to mix the two types, as this can be a cause of trouble.
EMM386 error messages refer to memory problems but may not be connected to bad Ram. This may be due to free memory problems often linked to old Dos-based programs.
BIOS settings
Every motherboard is supplied with a range of chipset settings that are decided in the factory. A common way to access these settings is to press the F2 or delete button during the first few seconds of a boot-up.
Once inside the BIOS, great care should be taken. It is a good idea to write down on a piece of paper all the settings that appear on the screen. That way, if you change something and the computer becomes more unstable, you will know what settings to revert to.
A common BIOS error concerns the CAS latency. This refers to the Ram. Older EDO (extended data out) Ram has a CAS latency of 3. Newer SDRam has a CAS latency of 2. Setting the wrong figure can cause the Ram to lock up and freeze the computer's display.
Microsoft Windows is better at allocating IRQ numbers than any BIOS. If possible set the IRQ numbers to Auto in the BIOS. This will allow Windows to allocate the IRQ numbers (make sure the BIOS setting for Plug and Play OS is switched to 'yes' to allow Windows to do this.).
Hard disk drives
After a few weeks, the information on a hard disk drive starts to become piecemeal or fragmented. It is a good idea to defragment the hard disk every week or so, to prevent the disk from causing a screen freeze. Go to
* Start-Programs-Accessories-System Tools-Disk Defragmenter
This will start the procedure. You will be unable to write data to the hard drive (to save it) while the disk is defragmenting, so it is a good idea to schedule the procedure for a period of inactivity using the Task Scheduler.
The Task Scheduler should be one of the small icons on the bottom right of the Windows opening page (the desktop).
Some lockups and screen freezes caused by hard disk problems can be solved by reducing the read-ahead optimisation. This can be adjusted by going to
* Start-Settings-Control Panel-System Icon-Performance-File System-Hard Disk.
Hard disks will slow down and crash if they are too full. Do some housekeeping on your hard drive every few months and free some space on it. Open the Windows folder on the C drive and find the Temporary Internet Files folder. Deleting the contents (not the folder) can free a lot of space.
Empty the Recycle Bin every week to free more space. Hard disk drives should be scanned every week for errors or bad sectors. Go to
* Start-Programs-Accessories-System Tools-ScanDisk
Otherwise assign the Task Scheduler to perform this operation at night when the computer is not in use.
Fatal OE exceptions and VXD errors
Fatal OE exception errors and VXD errors are often caused by video card problems.These can often be resolved easily by reducing the resolution of the video display. Go to
* Start-Settings-Control Panel-Display-Settings
Here you should slide the screen area bar to the left. Take a look at the color settings on the left of that window. For most desktops, high color 16-bit depth is adequate.
If the screen freezes or you experience system lockups it might be due to the video card. Make sure it does not have a hardware conflict. Go to
* Start-Settings-Control Panel-System-Device Manager
Here, select the + beside Display Adapter. A line of text describing your video card should appear. Select it (make it blue) and press properties. Then select Resources and select each line in the window. Look for a message that says No Conflicts.
If you have video card hardware conflict, you will see it here. Be careful at this point and make a note of everything you do in case you make things worse.
The way to resolve a hardware conflict is to uncheck the Use Automatic Settings box and hit the Change Settings button. You are searching for a setting that will display a No Conflicts message.
Another useful way to resolve video problems is to go to
* Start-Settings-Control Panel-System-Performance-Graphics
Here you should move the Hardware Acceleration slider to the left. As ever, the most common cause of problems relating to graphics cards is old or faulty drivers (a driver is a small piece of software used by a computer to communicate with a device).
Look up your video card's manufacturer on the internet and search for the most recent drivers for it.
Viruses
Often the first sign of a virus infection is instability. Some viruses erase the boot sector of a hard drive, making it impossible to start. This is why it is a good idea to create a Windows start-up disk. Go to
* Start-Settings-Control Panel-Add/Remove Programs
Here, look for the Start Up Disk tab. Virus protection requires constant vigilance.
A virus scanner requires a list of virus signatures in order to be able to identify viruses. These signatures are stored in a DAT file. DAT files should be updated weekly from the website of your antivirus software manufacturer.
An excellent antivirus program is McAfee Virus Scan by Network Associates ( www.nai.com). Another is Norton Antivirus 2000, made by Symantec ( www.symantec.com).
Printers
The action of sending a document to print creates a bigger file, often called a postscript file.
Printers have only a small amount of memory, called a buffer. This can be easily overloaded. Printing a document also uses a considerable amount of CPU power. This will also slow down the computer's performance.
If the printer is trying to print unusual characters, these might not be recognized, and can crash the computer. Sometimes printers will not recover from a crash because of confusion in the buffer. A good way to clear the buffer is to unplug the printer for ten seconds. Booting up from a powerless state, also called a cold boot, will restore the printer's default settings and you may be able to carry on.
Software
A common cause of computer crash is faulty or badly-installed software. Often the problem can be cured by uninstalling the software and then reinstalling it. Use Norton Uninstall or Uninstall Shield to remove an application from your system properly. This will also remove references to the program in the System Registry and leaves the way clear for a completely fresh copy.
The System Registry can be corrupted by old references to obsolete software that you thought was uninstalled. Use Registry Cleaner to clean up the System Registry and remove obsolete entries.
Often a Windows problem can be resolved by entering Safe Mode. This can be done during start-up. When you see the message "Starting Windows" press F4. This should take you into Safe Mode.
Safe Mode loads a minimum of drivers. It allows you to find and fix problems that prevent Windows from loading properly.
Sometimes installing Windows is difficult because of unsuitable BIOS settings. If you keep getting SUWIN error messages (Windows setup) during the Windows installation, then try entering the BIOS and disabling the CPU internal cache. Try to disable the Level 2 (L2) cache if that doesn't work.
Remember to restore all the BIOS settings back to their former settings following installation.
Overheating
Central processing units (CPUs) are usually equipped with fans to keep them cool. If the fan fails or if the CPU gets old it may start to overheat and generate a particular kind of error called a kernel error. This is a common problem in chips that have been overclocked to operate at higher speeds than they are supposed to.
One remedy is to get a bigger better fan and install it on top of the CPU. Specialist cooling fans/heatsinks are available from www.computernerd.com or www.coolit.com
CPU problems can often be fixed by disabling the CPU internal cache in the BIOS. This will make the machine run more slowly, but it should also be more stable.
Power supply problems
With all the new construction going on around the country the steady supply of electricity has become disrupted. A power surge or spike can crash a computer as easily as a power cut.
If this has become a nuisance for you then consider buying a uninterrupted power supply (UPS). This will give you a clean power supply when there is electricity, and it will give you a few minutes to perform a controlled shutdown in case of a power cut.
It is a good investment if your data are critical, because a power cut will cause any unsaved data to be lost.
I hope now you will be able to rectify your problems. keep reading and learning.
Labels:
LEARN HACKING - FOR BEGINNERS,
VISTA HACKS,
XP HACKS
Saturday, May 15, 2010
Hack your friends Internet Password
This is Really Amazing. I was moving through my Browser's settings and found the file where all the passwords are stored. I was really shocked that it allowed me to have a look at all the Username and Password which I had asked my computer to remember which also included my Internet Username and Password. But this is only possible in Mozila Firefox.
To Hack your friends Password you only need even less than a minute and you can have a quick look at your friends Usernames and Passwords.
Just follow the following steps:
1.Open Mozila Firefox
2.Goto Tools -> Options
3.In that goto Privacy -> Passwords.
4.There you will find View Saved Passwords Button Click on it.
5.It will show you a list of websites with the usernames. To get the Passwords Click on Show Passwords Button.
6.Now To get the Internet Password Just see for any IP address in the website column this is the Ip address of that computer and Username and Pass is what you want.
7.You can get pass of any account just look for the site name whose password you want to hack and on the right side you will get the Username and Password
How To: Change Your Ip In Less Then 1 Minute
This article will help you to change your IP address within a minute. Just follow the following step and you will be thru.
1. Click on "Start" in the bottom left hand corner of screen
2. Click on "Run"
3. Type in "command" and hit ok
You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here
14. Hit the "Ok" button again
You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings
17. This time, select "Obtain an IP address automatically"
tongue.gif 18. Hit "Ok"
19. Hit "Ok" again
20. You now have a new IP address
With a little practice, you can easily get this process down to 15 seconds.
P.S:
This only changes your dynamic IP address, not your ISP/IP address. If you plan on hacking a website with this trick be extremely careful, because if they try a little, they can trace it back
1. Click on "Start" in the bottom left hand corner of screen
2. Click on "Run"
3. Type in "command" and hit ok
You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here
14. Hit the "Ok" button again
You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings
17. This time, select "Obtain an IP address automatically"
tongue.gif 18. Hit "Ok"
19. Hit "Ok" again
20. You now have a new IP address
With a little practice, you can easily get this process down to 15 seconds.
P.S:
This only changes your dynamic IP address, not your ISP/IP address. If you plan on hacking a website with this trick be extremely careful, because if they try a little, they can trace it back
Wednesday, May 12, 2010
7 Must Have Tools For Every Hacker
Its been a while since I have posted about some hacking tools and with increasing number of emails asking me to do an article on it,I finally decided to cover it up.Hacking tools are developed by some really good coders out there to ease out many complex tasks which have to be done manually and took painstakingly great deal of time and effort.All these tools provided here are free of cost,are tried hands on and are being actively developed by community,and if not,their alternatives are provided.To summarize it up,these are the 7 must have tools for every hacker out there.
1. Nmap
I think everyone has heard of this one, it recently had a version 5 release.
Nmap (Network Mapper) is a free open source utility for network exploration or security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts.Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use,and dozens of other characteristics. It may be used to discover computers and services on a computer network, thus creating a "map" of the network.Nmap runs on most types of computers and both console and graphical versions are available. Nmap is free and open source.Can be used by beginners (-sT) or by pros alike (packet_trace). A very versatile tool, once you fully understand the results.
Download Nmap
2. Nessus Remote Security Scanner
Recently went closed source, but is still essentially free. Works with a client-server framework.Nessus is the worlds most popular vulnerability scanner used in over 75,000organizations world-wide. Many of the worlds largest organizations are realizing significant cost savings by using Nessus to audit business-critical enterprise devices and applications.
Download Nessus
3. Wireshark
If you have been reading my site,you might have read about it in a couple of articles.Wireshark is a GTK+-based network protocol analyzer, or sniffer, that lets you capture and interactively browse the contents of network frames. The goal of the project is to create a commercial-quality analyzer for Unix and to give Wireshark features that are missing from closed-source sniffers. Works great on both Linux and Windows (with a GUI), easy to use and can reconstruct TCP/IP Streams! .
Download Wireshark
4. Cain and Abel
The swiss knife of hacking tools..Cain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, revealing password boxes, uncovering cached passwords and analyzing routing protocols.The program does not exploit any software vulnerabilities or bugs that could not be fixed with little effort.
Download Cain and Abel
5. Kismet
Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Kismet will work with any wireless card which supports raw monitoring (rfmon) mode, and can sniff 802.11b, 802.11a, and 802.11g traffic. A good wireless tool as long as your card supports rfmon
Download Kismet
6. NetStumbler
Yes a decent wireless tool for Windows! Sadly not as powerful as it’s Linux counterparts, but it’s easy to use and has a nice interface, good for the basics of war-driving. NetStumbler is a tool for Windows that allows you to detect Wireless Local Area Networks (WLANs) using 802.11b, 802.11a and 802.11g. It has many uses:
1.Verify that your network is set up the way you intended.
2.Find locations with poor coverage in your WLAN.
3.Detect other networks that may be causing interference on your network.
4.Detect unauthorized rogue access points in your workplace.
5.Help aim directional antennas for long-haul WLAN links.
6.Use it recreationally for WarDriving.
Download NetStumbler
7. SuperScan
Powerful TCP port scanner, pinger, resolver. SuperScan 4 is an update of the highly popular Windows port scanning tool, SuperScan.If you need an alternative for nmap on Windows with a decent interface, I suggest you check this out, it’s pretty nice.
Download Superscan
Alternatively,you can try Angry IP Scanner which is a pretty good replacement for it.
1. Nmap
I think everyone has heard of this one, it recently had a version 5 release.
Nmap (Network Mapper) is a free open source utility for network exploration or security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts.Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use,and dozens of other characteristics. It may be used to discover computers and services on a computer network, thus creating a "map" of the network.Nmap runs on most types of computers and both console and graphical versions are available. Nmap is free and open source.Can be used by beginners (-sT) or by pros alike (packet_trace). A very versatile tool, once you fully understand the results.
Download Nmap
2. Nessus Remote Security Scanner
Recently went closed source, but is still essentially free. Works with a client-server framework.Nessus is the worlds most popular vulnerability scanner used in over 75,000organizations world-wide. Many of the worlds largest organizations are realizing significant cost savings by using Nessus to audit business-critical enterprise devices and applications.
Download Nessus
3. Wireshark
If you have been reading my site,you might have read about it in a couple of articles.Wireshark is a GTK+-based network protocol analyzer, or sniffer, that lets you capture and interactively browse the contents of network frames. The goal of the project is to create a commercial-quality analyzer for Unix and to give Wireshark features that are missing from closed-source sniffers. Works great on both Linux and Windows (with a GUI), easy to use and can reconstruct TCP/IP Streams! .
Download Wireshark
4. Cain and Abel
The swiss knife of hacking tools..Cain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, revealing password boxes, uncovering cached passwords and analyzing routing protocols.The program does not exploit any software vulnerabilities or bugs that could not be fixed with little effort.
Download Cain and Abel
5. Kismet
Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Kismet will work with any wireless card which supports raw monitoring (rfmon) mode, and can sniff 802.11b, 802.11a, and 802.11g traffic. A good wireless tool as long as your card supports rfmon
Download Kismet
6. NetStumbler
Yes a decent wireless tool for Windows! Sadly not as powerful as it’s Linux counterparts, but it’s easy to use and has a nice interface, good for the basics of war-driving. NetStumbler is a tool for Windows that allows you to detect Wireless Local Area Networks (WLANs) using 802.11b, 802.11a and 802.11g. It has many uses:
1.Verify that your network is set up the way you intended.
2.Find locations with poor coverage in your WLAN.
3.Detect other networks that may be causing interference on your network.
4.Detect unauthorized rogue access points in your workplace.
5.Help aim directional antennas for long-haul WLAN links.
6.Use it recreationally for WarDriving.
Download NetStumbler
7. SuperScan
Powerful TCP port scanner, pinger, resolver. SuperScan 4 is an update of the highly popular Windows port scanning tool, SuperScan.If you need an alternative for nmap on Windows with a decent interface, I suggest you check this out, it’s pretty nice.
Download Superscan
Alternatively,you can try Angry IP Scanner which is a pretty good replacement for it.
How to Alter Windows Product ID
If you are running a Microsoft Windows operating system on your computer, then you are most likely aware of the fact that your PC will have a Product ID. This Product ID is a system specific alphanumeric code which is derived/calculated based on the Windows product key you use and the hardware configuration of your Computer. In simple words, Product ID is the alphanumeric code that you see when you Right-Click on the My Computer icon and select the Properties option.
Ever wondered how to alter the Windows Product ID?
It is possible to alter the Windows Product ID and change it to what ever you like. For example, you can change the Product ID and put your nickname in place of the formal Product ID displayed by the Operating System. This hack is too easy and can be done within minutes. The screenshot showing the altered Product ID is given below
Win 7 PC showing Original PID
Windows 7 PC showing Altered PID
As you can see from the above screenshot it is simple and easy to make your Windows display what ever you want in the place of the real Product ID. Here is a step-by-step procedure to alter your Windows Product ID.
1. Goto Start->Run and type the following in the Run dialog box
regedit
2. After you open the Registry Editor, navigate to the following key
HKey_Local_Machine\Software\Microsoft\Windows NT\Current Version
3. On the right hand side, you can see an entry by name ProductID listed under the heading Name.
4. Double-Click on ProductID, a dialog box will pop-up showing your Windows PID. Now you can delete the original PID and enter anything of your choice.
5. Once you are done, just click on OK and close the Registry Editor. Now you can see the altered Product ID in the Windows Properties window.
NOTE: This trick works on Win 7, Vista and Win XPI hope you like this trick. Pass your comments. Cheers!
Ever wondered how to alter the Windows Product ID?
It is possible to alter the Windows Product ID and change it to what ever you like. For example, you can change the Product ID and put your nickname in place of the formal Product ID displayed by the Operating System. This hack is too easy and can be done within minutes. The screenshot showing the altered Product ID is given below
Win 7 PC showing Original PID
Windows 7 PC showing Altered PID
As you can see from the above screenshot it is simple and easy to make your Windows display what ever you want in the place of the real Product ID. Here is a step-by-step procedure to alter your Windows Product ID.
1. Goto Start->Run and type the following in the Run dialog box
regedit
2. After you open the Registry Editor, navigate to the following key
HKey_Local_Machine\Software\Microsoft\Windows NT\Current Version
3. On the right hand side, you can see an entry by name ProductID listed under the heading Name.
4. Double-Click on ProductID, a dialog box will pop-up showing your Windows PID. Now you can delete the original PID and enter anything of your choice.
5. Once you are done, just click on OK and close the Registry Editor. Now you can see the altered Product ID in the Windows Properties window.
NOTE: This trick works on Win 7, Vista and Win XPI hope you like this trick. Pass your comments. Cheers!
Labels:
LEARN HACKING - FOR BEGINNERS,
VISTA HACKS,
XP HACKS
Saturday, May 1, 2010
Super Bluetooth Hack 2008(Latest Version)
This is a New Version of Super Bluetooth Hack for Conventional and Mobile-based Symbian. This program through MDM can be used to control other people’s mobile phone at a distance (10-15 metres, it’s Then)
Super Bluetooth hack New 2008
More in New Version :
1) Connect via BT/Irda
2) Reading SMS
3) Changing time/alarms
4) Pressing keys…
What else can you do once connected to a another phone via blue tooth?
1) Read SMS matches.
2) Turn off telephone.
3) Switch on music.
4) Choose modes (normal, without sound …)
5) Block Phone.
6) Read his Contacts
7) Change Profile
Play his Ringtone even if phone is on silent
9) Restore Factory Settings.
10) Restart the phone
11) Change Ringing Volume
And here comes the best
“Call from his phone” it includes all call functions like hold etc.
And much, much more
Install:
1) Download
2) Pour on the mobile
3) Run the Installer (what you download, incidentally need JAVA)
4) He finds it, and you will be able to run software
5) Choose the language and going configured
6) Click Connection
7) Click search devices
Choose the “victim”
9) AND MANAGE
Download
Password : www.dl4all.com
Super Bluetooth hack New 2008
More in New Version :
1) Connect via BT/Irda
2) Reading SMS
3) Changing time/alarms
4) Pressing keys…
What else can you do once connected to a another phone via blue tooth?
1) Read SMS matches.
2) Turn off telephone.
3) Switch on music.
4) Choose modes (normal, without sound …)
5) Block Phone.
6) Read his Contacts
7) Change Profile
Play his Ringtone even if phone is on silent
9) Restore Factory Settings.
10) Restart the phone
11) Change Ringing Volume
And here comes the best
“Call from his phone” it includes all call functions like hold etc.
And much, much more
Install:
1) Download
2) Pour on the mobile
3) Run the Installer (what you download, incidentally need JAVA)
4) He finds it, and you will be able to run software
5) Choose the language and going configured
6) Click Connection
7) Click search devices
Choose the “victim”
9) AND MANAGE
Download
Password : www.dl4all.com
How does Worms work ?
People use e-mail more than any other application on the internet, but it can be a frustrating experience, with spam and especially e-mail worms filling our inboxes.
Worms can spread rapidly over computer networks, the traffic they create bringing those networks to a crawl. And worms can cause other damage, such as allowing unauthorized access to a computer network, or deleting or copying files.
What's a worm?
A worm is a computer virus designed to copy itself, usually in large numbers, by using e-mail or other form of software to spread itself over an internal network or through the internet.
How do they spread?
When you receive a worm over e-mail, it will be in the form of an attachment, represented in most e-mail programs as a paper clip. The attachment could claim to be anything from a Microsoft Word document to a picture of tennis star Anna Kournikova (such a worm spread quickly in February 2001).
If you click on the attachment to open it, you'll activate the worm, but in some versions of Microsoft Outlook, you don't even have to click on the attachment to activate it if you have the program preview pane activated. Microsoft has released security patches that correct this problem, but not everyone keeps their computer up to date with the latest patches.
After it's activated, the worm will go searching for a new list of e-mail addresses to send itself to. It will go through files on your computer, such as your e-mail program's address book and web pages you've recently looked at, to find them.
Once it has its list it will send e-mails to all the addresses it found, including a copy of the worm as an attachment, and the cycle starts again. Some worms will use your e-mail program to spread themselves through e-mail, but many worms include a mail server within their code, so your e-mail program doesn't even have to be open for the worm to spread.
Other worms can use multiple methods of spreading. The MyDoom worm, which started spreading in January 2004, attempted to copy infected files into the folder used by Kazaa, a file-sharing program. The Nimda worm, from September 2001, was a hybrid that had four different ways of spreading.
What do they do?
Most of the damage that worms do is the result of the traffic they create when they're spreading. They clog e-mail servers and can bring other internet applications to a crawl.
But worms will also do other damage to computer systems if they aren't cleaned up right away. The damage they do, known as the payload, varies from one worm to the next.
The MyDoom worm was typical of recent worms. It opened a back door into the infected computer network that could allow unauthorized access to the system. It was also programmed to launch an attack against a specific website by sending thousands of requests to the site in an attempt to overwhelm it.
The target of the original version of MyDoom attack was the website of SCO Group Inc., a company that threatened to sue users of the Linux operating system, claiming that its authors used portions of SCO's proprietary code. A second version of MyDoom targeted the website of software giant Microsoft.
The SirCam worm, which spread during the summer of 2001, disguised itself by copying its code into a Microsoft Word or Excel document and using it as the attachment. That meant that potentially private or sensitive documents were being sent over the internet.
How do I get rid of them?
The best way to avoid the effects of worms is to be careful when reading e-mail. If you use Microsoft Outlook, get the most recent security updates from the Microsoft website and turn off the preview pane, just to be safe.
Never open attachments you aren't expecting to receive, even if they appear to be coming from a friend. Be especially cautious with attachments that end with .bat, .cmd, .exe, .pif, .scr, .vbs or .zip, or that have double endings. (The file attachment that spread the Anna Kournikova worm was AnnaKournikova.jpg.vbs.)
Also, install anti-virus software and keep it up to date with downloads from the software maker's website. The updates are usually automatic.
Users also need to be wary of e-mails claiming to have cures for e-mail worms and viruses. Many of them are hoaxes that instruct you to delete important system files, and some carry worms and viruses themselves.
As well, some users should consider using a computer with an operating system other than Windows, the target of most e-mail worms. Most of the worms don't affect computers that run Macintosh or Linux operating systems.
downloads
Norton AntiVirus 2010 17.6.0.32 download
Kaspersky Internet Security 2011 11.0.0.187 Beta download
Avira Premium Security Suite 10.0.0.542 download
Norton Internet Security 2011 18.0.0.42 Beta download
Avast! Free Antivirus 5.0.507 download
Norton 360 v4.1.0.32 part1 part2
AVG Anti-Virus plus Firewall 9.0.800 Build 2779 download
AVG Internet Security 9.0.800 Build 2779 download
ZoneAlarm AntiVir 9.1.507.000 2010 download

PCRecovery DriveRestore Professional v3.1.2 download
AIO Dr.Web Software Package 25.04.2010 (Multi) download
Stellar Phoenix Windows Data Recovery 4.1.0.1 download
iCare Data Recovery Software v3.5 download
Realtek High Definition Audio Driver R2.47
for xp/vista/7 download
Driver Genius Professional 2009 9.0.0.189 download
Drivers Pack 2009 9.2 - 32Bit parts 1, 2, 3, 4, 5
100.000 Drivers For
VISTA/XP/ME/98/95/2000/2003/ parts 1,2,3,4,5, 6,7,8

Internet Download Manager 5.19 Pre-Cracked download
Free Download Manager 3.4.902a Portable download
Rapidshare Direct Download Manager Portable download
youtube downloader download

Internet Explorer 8 Beta download
google chrome download
opera browser download
mozilla firefox download

klite codec pack download
xp codec pack download
xvid,divx codec download

ImTOO YouTube Video Converter download
pspvc(convert to psp format) download
imtoo video converter(platinum) download
(serial key:www.2baksa.net)
Nero 10 Portable download
Nero 9.2.6.0 Ultra/Lite/Micro Edition parts 1, 2
cd burner xp download
secret mobile codes download
unlock all mobile phones download
Mobile Master 7.6 Build 3238 - Final download
Kaspersky Mobile Security ( S60 ) download
Mobile Tracking System 1.51 download
S60V5 Programes mobile download
iPhone 3G Firmware 3.1.3 7E18 parts 1,2 ,3
magicbluehack.jar download
Java Games Collection parts 1, 2

microsoft office 2007 download
Encrypt USB Flash Drive with BitLocker
Since Windows Vista has been released, BitLocker was introduced to Windows User. But, in Windows Vista, BitLocker only support to encrypt internal hard drive. Now, BitLocker is also supported on Windows 7. It supports to encrypt removable disk, such USB Flash Drive. Using BitLocker on a removable USB flash drive provides a great way to protect your data in the event the drive was lost or stolen.
Do I can access the data if the drive is protected by BitLocker? Yes. You can access your data on Windows XP and Vista through a read-only interface that is installed during the initial encryption. So, you are able to get your data on other Windows Version, not just on your Windows 7 computer.
How to start encrypting a removable drive using BitLocker? Here’s the steps how to encrypt USB Flash drive with BitLocker:
1.Plug in your USB flash drive into computer. Then, right click on your drive through Windows Explorer and select Turn on BitLocker.
2.Next, check one of two options provides. You can set a password to protect the drive or use a smart card if your device has a smart card reader. Because my drive does not use smart card, so I choose the first options. Click Next to continue to the next step.
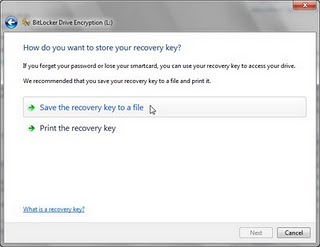
3.On the next Windows, you will asked to recover the key if you forget the password or lose the smart card. So I recomended you to save the recovery key to a file. Click Next to start Start the Encryption.
Now, the Encryption will be started. It can take a few minutes to complete it. Depending on the size of your USB flash drive. The drive will be protected whe the encryption completed and you can plug off the USB flash drive from your computer.
Now, I will show you how to use the encrypted USB flash drive on another computer with different operating system, for example in Windows XP computer.
1.First, plug the the encrypted USB falsh drive.
2.Open the Windows Explorer, the you will see the USB flash drive will have a different icon. Double klik the drive the execute BitLockerToGo.exe.
3.After you execute it, you will be asked for the password. Type in your password.
4.Once authenticated, a read-only Windows will appear where you can see the encrypted files.
In order to modify the files, you need to extract it first from the encrypted USB flash drive.
Do I can access the data if the drive is protected by BitLocker? Yes. You can access your data on Windows XP and Vista through a read-only interface that is installed during the initial encryption. So, you are able to get your data on other Windows Version, not just on your Windows 7 computer.
How to start encrypting a removable drive using BitLocker? Here’s the steps how to encrypt USB Flash drive with BitLocker:
1.Plug in your USB flash drive into computer. Then, right click on your drive through Windows Explorer and select Turn on BitLocker.
2.Next, check one of two options provides. You can set a password to protect the drive or use a smart card if your device has a smart card reader. Because my drive does not use smart card, so I choose the first options. Click Next to continue to the next step.
3.On the next Windows, you will asked to recover the key if you forget the password or lose the smart card. So I recomended you to save the recovery key to a file. Click Next to start Start the Encryption.
Now, the Encryption will be started. It can take a few minutes to complete it. Depending on the size of your USB flash drive. The drive will be protected whe the encryption completed and you can plug off the USB flash drive from your computer.
Now, I will show you how to use the encrypted USB flash drive on another computer with different operating system, for example in Windows XP computer.
1.First, plug the the encrypted USB falsh drive.
2.Open the Windows Explorer, the you will see the USB flash drive will have a different icon. Double klik the drive the execute BitLockerToGo.exe.
3.After you execute it, you will be asked for the password. Type in your password.
4.Once authenticated, a read-only Windows will appear where you can see the encrypted files.
In order to modify the files, you need to extract it first from the encrypted USB flash drive.
The Top 5 Tips and Tricks To Unlock Vista’s Potential
Windows Vista has a large amount of options when it comes to customization, as do nearly all Windows operating systems. Fortunately, Vista makes it even easier then you may believe to tweak your operating system.
Today, we will be looking at some of the top Vista tricks to increase productivity and unlock Vista’s potential. Here they are (in no particular order):
Access Vista’s Super User Mode
Vista is riddled with an extremely large amount of “security” measures that may, or may not, be helpful. Running Vista as an Administrator may help, but did you know there is an even higher Administrator? Well, there is! All you need to do to unlock it is the following:
Step One: Go to “Start” and type cmd.
Step Two: When the command prompt loads, type the following:
Net user Administrator /active:yes
Step Three: When you switch user, you should now be able to see an Administrator account.
(Note: If you would like to hide the Administrator account, you can, again, go to “Start” and type cmd, then type: Net user administrator /active:no)
Save Battery Life on Laptops
Vista is quite a resource hog. If you have a laptop, this could present a problem. To maximize battery life and still run Vista on a viable amount of memory, simply do the following:
Step One: Hit the Windows Key and X at the same time.
Step Two: When “Windows Mobility Center” loads, you should be able to adjust settings, such as Display Brightness, Power Consumption, etc.
Remove Personal Information from Files
Nearly every single file on your computer contains some type of personal information – either information about the user, information on setting e.g. time, date, etc. In any case, it may be good to remove some of this information before making it available to the public, such as uploading a video or image online.
To do this, all you need to do is:
Step One: Select one or multiple file(s)
Step Two: Right-Click and select “Properties”
Step Three: Click “Details” and then click “Remove Properties and Personal Information.”
You can now have Vista create copies of the selected file(s) before changing/removing any of the information.
Tweaking Windows Power Button
Unlike Windows XP, the Vista power off button simply puts your computer to sleep when you were actually intending to turn it off. Fortunately, this can be easily changed with a simple tweak.
Step One: Click “Start,” then click “Control Panel."
Step Two: Select “Hardware and Sound,” then click “Power Options.”
Step Three: Click “Change Plan Settings” under your current power plan.
Step Four: Click “Change Advanced Settings,” and then navigate to:
Power Buttons and Lid / Start Menu Power Button
Step Five: Select “Shut Down”
Disable UAC Notification Messages
One of the most ridiculous features of Vista are the continuous “confirmation” messages. Messages that pop up nearly every time you attempt to run any unknown application. Almost all of which are completely unnecessary, and waste time. Here is how you can disable these annoying uac notifications, quickly and easily:
Step One: Go to “Start” and click “Control Panel.”
Step Two: Click “User Accounts and Family Safety,” then click “Turn User Account Control On and Off.”
Step Three: Un-Select the box labeled User User Account Control (UAC) to help protect my computer.
Step Four: Click “OK,” and you’re done!
Alternatively, you can check out Norton’s UAC Tool (previously covered by MakeUseOf author Karl Gechlik) that can hlp you deal with those warning in a more manageable way.
Hope this helps some of you get that much closer to a nearly perfectly tweaked computer.
Stay tuned for more WinHack!
Today, we will be looking at some of the top Vista tricks to increase productivity and unlock Vista’s potential. Here they are (in no particular order):
Access Vista’s Super User Mode
Vista is riddled with an extremely large amount of “security” measures that may, or may not, be helpful. Running Vista as an Administrator may help, but did you know there is an even higher Administrator? Well, there is! All you need to do to unlock it is the following:
Step One: Go to “Start” and type cmd.
Step Two: When the command prompt loads, type the following:
Net user Administrator /active:yes
Step Three: When you switch user, you should now be able to see an Administrator account.
(Note: If you would like to hide the Administrator account, you can, again, go to “Start” and type cmd, then type: Net user administrator /active:no)
Save Battery Life on Laptops
Vista is quite a resource hog. If you have a laptop, this could present a problem. To maximize battery life and still run Vista on a viable amount of memory, simply do the following:
Step One: Hit the Windows Key and X at the same time.
Step Two: When “Windows Mobility Center” loads, you should be able to adjust settings, such as Display Brightness, Power Consumption, etc.
Remove Personal Information from Files
Nearly every single file on your computer contains some type of personal information – either information about the user, information on setting e.g. time, date, etc. In any case, it may be good to remove some of this information before making it available to the public, such as uploading a video or image online.
To do this, all you need to do is:
Step One: Select one or multiple file(s)
Step Two: Right-Click and select “Properties”
Step Three: Click “Details” and then click “Remove Properties and Personal Information.”
You can now have Vista create copies of the selected file(s) before changing/removing any of the information.
Tweaking Windows Power Button
Unlike Windows XP, the Vista power off button simply puts your computer to sleep when you were actually intending to turn it off. Fortunately, this can be easily changed with a simple tweak.
Step One: Click “Start,” then click “Control Panel."
Step Two: Select “Hardware and Sound,” then click “Power Options.”
Step Three: Click “Change Plan Settings” under your current power plan.
Step Four: Click “Change Advanced Settings,” and then navigate to:
Power Buttons and Lid / Start Menu Power Button
Step Five: Select “Shut Down”
Disable UAC Notification Messages
One of the most ridiculous features of Vista are the continuous “confirmation” messages. Messages that pop up nearly every time you attempt to run any unknown application. Almost all of which are completely unnecessary, and waste time. Here is how you can disable these annoying uac notifications, quickly and easily:
Step One: Go to “Start” and click “Control Panel.”
Step Two: Click “User Accounts and Family Safety,” then click “Turn User Account Control On and Off.”
Step Three: Un-Select the box labeled User User Account Control (UAC) to help protect my computer.
Step Four: Click “OK,” and you’re done!
Alternatively, you can check out Norton’s UAC Tool (previously covered by MakeUseOf author Karl Gechlik) that can hlp you deal with those warning in a more manageable way.
Hope this helps some of you get that much closer to a nearly perfectly tweaked computer.
Stay tuned for more WinHack!
Speed-up Windows Vista's Aero
Windows Vista is a step-up in terms of eye candy but it can slow your system down a bit. There are 2 things you can do to speed-up the Aero interface in Windows Vista:
Method 1: Disable Transparent Glass Effect
1. Click on the Desktop and select Personalize.
2. Select Windows Color And Appearance.
3. Uncheck Enable Transparency.
Method 2: Disable Windows Minimize/Maximize Animation
1. Click on the Start Menu, enter SystemPropertiesPerformance and hit Enter.
2. On the Visual Effects tab, uncheck Animate Windows When Minimizing/Maximizing.
3. Click OK.
Method 1: Disable Transparent Glass Effect
1. Click on the Desktop and select Personalize.
2. Select Windows Color And Appearance.
3. Uncheck Enable Transparency.
Method 2: Disable Windows Minimize/Maximize Animation
1. Click on the Start Menu, enter SystemPropertiesPerformance and hit Enter.
2. On the Visual Effects tab, uncheck Animate Windows When Minimizing/Maximizing.
3. Click OK.
USB Storage & Windows Vista ReadyBoost
Windows Vista has a new performance feature called ReadyBoost. This feature enables the use of a USB storage device instead of the slow paging file on your hard disk when you're low on physical memory (RAM). The logic is simple - the USB storage device is faster than your hard disk drive.
In order for ReadyBoost to work in Windows Vista, your USB storage device must meet the following requirements:
- the device must have at least 64MB storage.
- the device must be USB 2.0 compliant.
- the device must have a minimum read speed of 3.5 MB/s.
- the device must have a minimum write speed of 2.5 MB/s.
Follow these steps to enable ReadyBoost:
1. Plug in USB storage device.
2. Go to Computer, right-click on the removable storage device and select Properties.
3. Click on the ReadyBoost tab.
4. Select Use This Device and set the amount of space to use for the system file.
5. Click OK.
20 registry hacks to make your comp awesome
Right-clicking on everything is a good way to learn about hidden Windows functionality. Exploring the lesser-known Control Panel applets is another useful technique, and browsing the command line applications in Windows' System32 folder can be interesting. But let's be realistic. There's nothing that quite compares to the Registry.
It's packed with useful settings that can improve performance, fix security holes and change even the most fundamental Windows behaviour for the better. And many of these features simply can't be accessed in any other way. Be careful, though: the Registry has more than its fair share of traps.
If you're not cautious, you could cause more problems than you solve. But with a little care you can get on with creating a better system that's tailored towards your needs. Here are 20 great Registry hacks that everyone should know about.
1. Improve security
If strangers have physical access to your PC, it's easy for them to plug in a USB flash drive and make copies of your data. If you're using Windows XP SP2 or later, though, there's a simple way to prevent this from happening.
Go to 'HKLM\SYSTEM\CurrentControlSet\Control\StorageDevicePolicies', create a DWORD value called 'WriteProtect' and set it to 1. You'll be able to read USB drives, but not write to them any more.
2. Tame UAC
Windows Vista's User Account Control raises so many alerts that many people just turn it off. But do that and you'll also lose useful features like IE's protected mode. If you really can't live with UAC, try disabling the alerts for administrators: you won't get any more hassle, but UAC will run in the background and you'll still get its other features.
To do this, set 'HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorAdmin' to 0. You can restore normal UAC behaviour by setting it to 2.
3. Change the owner
Install Windows on your PC and you'll be asked to enter your name, which is then stored as the registered owner (run WinVer to see this on your system). If you've got a second-hand PC, you probably want to change the name stored as the registered owner. There's no obvious way to do this, and that's where the Registry comes in.
Browse to 'HKLM\SOFTWARE\Microsoft\WindowsNT\CurrentVersion' and you'll see both a 'RegisteredOwner' and 'RegisteredOrganization' value. Double-click either to change them.
4. Sort files properly
Sorting filenames in Explorer can be a problem. By default, it will place 'File_v2.txt' before 'File_v15. txt': that's not ASCII ordering, but it seems to be sensible. But what if the 'v' refers to a version number, and actually File_v15.txt should come first? Suddenly Explorer's default system doesn't work at all.
To restore regular ASCII file ordering, go to 'HKLM\Software\Microsoft\Windows\Currentversion\Policies\Explorer', create a DWORD value called 'NoStrCmpLogical' and set it to 1. Delete the key to restore the standard Explorer approach.
5. Troubleshoot startup
If Windows is taking its time to start up or shut down, there might be a problem. To find out what's going on, go to 'HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System', create a DWORD value called 'verbosestatus' and set it to 1. Restart your PC and Windows will tell you what it's getting up to.
6. Manage folder types
Windows Vista's Explorer will 'intelligently' choose your folder type based on its contents. But this means that a Download folder will change to a Music folder if you grab a few MP3s. To fix this, go to 'HCU\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell', delete the 'Bags' subkey and then create a new Bags key in the same location.
Create a key called 'AllFolders' beneath Bags, and a key called 'Shell' below that. Click it to open 'HCU\Software\Classes\LocalSettings\Software\Microsoft\Windows\Shell\ Bags\AllFolders\Shell'. Right-click the right-hand pane, choose 'New
String Value' and call this 'FolderType'. Then double-click FolderType and set its value to 'NotSpecified'. You'll still be able to change the folder type, but Vista will no longer assign one. (See steps 10 to 20 here if you need more help.)
7. Easy encryption
Some versions of Windows have always allowed you to encrypt files, but it's an awkward process; you must right-click the file, select 'Properties', click the 'Advanced' button, check 'Encrypt contents to secure data' and then press 'OK' twice.
For a simpler alternative, go to 'HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced', create a new DWORD called 'EncryptionContextMenu' and set it to 1. Now you can just right-click a file and select 'Encrypt'.
8. Access folders fast
Get speedy access to any folder by pinning it to the Start menu. Run REGEDIT, go to 'HKCR\Folder\shellex\ContextMenuHandlers', right-click 'ContextMenuHandlers' and click 'New
Key'.
Type '' (as ever, without quotation marks) and press [Enter]. Now hold down [Shift], right-click a folder and select 'Pin to Start Menu'.
9. Speed up copy times
Vista gives a high priority to your soundcard, so you should get glitch-free audio no matter what you're doing. This can cause slower network copy speeds, however.
To tweak this, browse to 'HKLM\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Multimedia\SystemProfile'. Try setting 'NetworkThrottlingIndex' to more than 10 – 50 or 60 should be effective – then reboot and test your network speeds again. Read more here.
10. Fix the drive listing
If Explorer no longer lists your DVD drive (or thinks that it's a DVD-ROM and can't burn discs), go to 'HKLM\System\CurrentControlSet\Control\Class\' and delete the 'UpperFilters' or 'LowerFilters' settings.
This usually works, but it may break whatever application caused the problem in the first place. If a program stops working, check to see if it has an update, then reinstall it
11. Access display settings quickly
Right-click the desktop in Windows Vista and you can't directly access the display settings. Windows 7 will fix this, but in the meantime go to 'HKCR\Directory\Background\Shell', right-click 'Shell', select 'New
Key' and call it 'Display Settings'.
Double-click '(Default)' in the right-hand pane and enter 'Display Settings' in the Value Data box. Now right-click Display Settings in the left-hand pane, select 'New
Key' again and call this key 'command'.
Double-click this new key's (Default) value and enter this text: 'rundll32 shell32.dll,Control_ RunDLL DESK.CPL,@0,3'. (That's a zero following the @ sign, and take care to use the right cases.) Click 'OK' and right-click the desktop to see the new Display Settings option.
12. Multiple Live Messenger log-ins
By default, Windows Live Messenger only lets you log into one account at a time. To rectify this situation, go to 'HKLM\Software\Microsoft\WindowsLive\Messenger', create a DWORD value called 'Multiple Instances' and set it to 1. Delete the value to restore things to the way they were beforehand.
13. Clean the menus
You've uninstalled an application, but it's left you a gift: several now-useless right-click context menu entries. To fix this, go to 'HKCR\*' and 'HKCR\Directory'. Expand the shell, then the 'shellex\ContextMenuHandlers' keys and look for any keys beneath these that relate to your unwanted command.
On our PC, the key 'HKCR\*\shellex\ContextMenuHandlers\7-Zip' links to the 7-Zip context menu, for instance, so to get rid of that we would right-click the 7-Zip part in the left-hand pane and click 'Delete'. But be careful – only delete a key if you're really sure it's the right one.
14. Speed up backups
Windows XP's NTBACKUP improves its performance by maintaining a list of system files it knows you won't want to back up (such as the paging file). Add your own files and folders that you're not bothered about and you'll get even better results.
View the list at 'HKLM\SYSTEM\CurrentControlSet\Control\BackupRestore\FilesNotToBackup'.
15. Change the default installation folder
Most installations default to the Program Files folder, but if you want to point this elsewhere, navigate to 'HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion', change the 'ProgramFilesDir' entry to point at your chosen folder and reboot.
16. Rename drives
Add a memory card reader to a PC and Explorer will often cram the Computer folder with similar sounding drive names ('Removable Drive D:', 'Removable Drive E:' and so on), making it difficult to tell them apart. But it doesn't have to be that way.
If drive G: is a CompactFlash slot, say, then a few Registry tweaks can change it to read 'CompactFlash (G:)', making things much clearer. Start at 'HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer' and create a key called 'DriveIcons'.
Within that, create a key with the drive letter ('G' in this example), and within that, create a new key called 'DefaultLabel'. Double-click this key's (Default) value entry, give it the name 'CompactFlash' (or whatever you like) and click 'OK'. Restart Explorer or press [F5] to see the change.
17. Wipe the page file
Windows stores memory pages in its paging file as you work. That's fine unless an intruder gets access to your system. If so, they may then be able to browse the paging file and extract confidential information.
To avoid this, go to 'HKLM\SYSTEM\CurrentControlSet\Control\SessionManager\MemoryManagement', set the 'ClearPageFileAtShutdown' value to 1 and reboot. Windows will now wipe the page file every time it shuts down, lengthening the process but increasing your security.
18. Crash on cue
Blue-screen crashes are usually bad news, but occasionally you might want to initiate one yourself. You might need to test Windows' error reporting, for example. There's a Registry trick that can help achieve this.
Go to 'HKLM\SYSTEM\CurrentControlSet\Services\i8042prt\Parameters', create a DWORD called 'CrashOnCtrlScroll' and set it to 1. Reboot your computer, and to crash it just hold down the right [CTRL] and press [Scroll Lock] twice. Use this sparingly: it's a crash like any other, and there's a chance of hard drive corruption. To be safe, delete the CrashOnCtrlScroll value when you're done.
19. Save CPU time
The average PC has several programs wanting to use the processor at any one time, and so Windows allocates each a period of CPU time – a 'quantum' – before moving to the next. By default this is very short, which makes for a responsive PC, but it sometimes means that Windows wastes time just switching between processes.
The solution? You can try what Windows Server does: set up your system to use a long quantum. Set 'HKLM\SYSTEM\CurrentControlSet\Control\PriorityControl\Win32PrioritySeparation' to 16 (hex).
Longer quantums mean fewer switches between programs and so less wasted time. It can push some programs too far, though, and you might begin to notice games lagging or video playback becoming less smooth. If you spot any problems, just restore the original Win32PrioritySeparation value (probably 26 hex).
20. Disable AutoRun
Windows' AutoRun feature is a potential security risk because it automatically runs code when you connect removable devices to your PC. If you can put up with the inconvenience of doing things manually then it's safest to disable it.
On some systems, this can only be done from the Registry. To do so, go to 'HKLM\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\IniFileMapping' and create a key called 'Autorun.inf'.
Next, double-click the new key's (Default) value and enter the new value '@SYS:DoesNotExist'. Now delete the Registry key 'HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2'. Windows now won't automatically run any code on CDs, DVDs or removable drives; you will have to manually launch it