Monday, June 28, 2010
How to Display Selected Friends Only on your Facebook Profile Page
While many facebook users have hundreds, if not thousands of facebook friends Some people may find they are looking at random faces from years gone by every time the look at there facebook profile. This neat little trick will show you how to display certain friends that you select all the time on your facebook profile. You can also select how many friends are shown.
A little-known feature in Facebook that enables you to decide who shows up in that Friends box on your facebook profile page. Click that “edit” pencil in your Friends box and type the names of your best friends in the box that says “Always show these friends”
Facebook is full of little known tricks like this and it is obvious when you know its there but untill you know it is a secret.
How to Hack an Ethernet ADSL Router
Almost half of the Internet users across the globe use ADSL routers/modems to connect to the Internet however, most of them are unaware of the fact that it has a serious vulnerability which can easily be exploited even by a noob hacker just like you. In this post I will show you how to exploit a common vulnerability that lies in most ADSL routers so as to gain complete access to the router settings and ISP login details.
Every router comes with a username and password using which it is possible to gain access to the router settings and configure the device. The vulnerability actually lies in the Default username and password that comes with the factory settings. Usually the routers come preconfigured from the Internet Service provider and hence the users do not bother to change the password later. This makes it possible for the attackers to gain unauthorized access and modify the router settings using a common set of default usernames and passwords. Here is how you can do it.
Before you proceed, you need the following tool in the process
Angry IP Scanner
Here is a detailed information on how to exploit the vulnerability of an ADSL router.
Step-1: Go to www.whatismyipaddress.com. Once the page is loaded you will find your IP address. Note it down.
Step-2: Open Angry IP Scanner, here you will see an option called IP Range: where you need to enter the range of IP address to scan for.
Suppose your IP is 117.192.195.101, you can set the range something as 117.192.194.0 to 117.192.200.255 so that there exists atleast 200-300 IP addresses in the range.
Step-3: Go to Tools->Preferences and select the Ports tab. Under Port selection enter 80 (we need to scan for port 80). Now switch to the Display tab, select the option “Hosts with open ports only” and click on OK.
I have used Angry IP Scanner v3.0 beta-4. If you are using a different version, you need to Go to Options instead of Tools
Step-4: Now click on Start. After a few minutes, the IP scanner will show a list of IPs with Port 80 open as shown in the below image.
Step-5: Now copy any of the IP from the list, paste it in your browser’s address bar and hit enter. A window will popup asking for username and password. Since most users do not change the passwords, it should most likely work with the default username and password. For most routers the default username-password pair will be admin-admin or admin-password.
Just enter the username-password as specified above and hit enter. If you are lucky you should gain access to the router settings page where you can modify any of the router settings. The settings page can vary from router to router. A sample router settings page is shown below.
If you do not succeed to gain access, select another IP from the list and repeat the step-5. Atleast 1 out of 5 IPs will have a default password and hence you will surely be able to gain access.
What can an Attacker do by Gaining Access to the Router Settings?
By gaining access to the router settings, it is possible for an attacker to modify any of the router settings which results in the malfunction of the router. As a result the target user’s computer will be disconnected from the Internet. In the worst case the attacker can copy the ISP login details from the router to steal the Internet connection or play any kind of prank with the router settings. So the victim has to reconfigure the router in order to bring it back to action.
The Verdict:
If you are using an ADSL router to connect to the Internet, it is highly recommended that you immediately change your password to prevent any such attacks in the future. Who knows, you may be the next victim of such an attack.
Since the configuration varies from router to router, you need to contact your ISP for details on how to change the password for your model.
Warning!
All the information provided in this post are for educational purposes only. Please do not use this information for illegal purposes.
.
Every router comes with a username and password using which it is possible to gain access to the router settings and configure the device. The vulnerability actually lies in the Default username and password that comes with the factory settings. Usually the routers come preconfigured from the Internet Service provider and hence the users do not bother to change the password later. This makes it possible for the attackers to gain unauthorized access and modify the router settings using a common set of default usernames and passwords. Here is how you can do it.
Before you proceed, you need the following tool in the process
Angry IP Scanner
Here is a detailed information on how to exploit the vulnerability of an ADSL router.
Step-1: Go to www.whatismyipaddress.com. Once the page is loaded you will find your IP address. Note it down.
Step-2: Open Angry IP Scanner, here you will see an option called IP Range: where you need to enter the range of IP address to scan for.
Suppose your IP is 117.192.195.101, you can set the range something as 117.192.194.0 to 117.192.200.255 so that there exists atleast 200-300 IP addresses in the range.
Step-3: Go to Tools->Preferences and select the Ports tab. Under Port selection enter 80 (we need to scan for port 80). Now switch to the Display tab, select the option “Hosts with open ports only” and click on OK.
I have used Angry IP Scanner v3.0 beta-4. If you are using a different version, you need to Go to Options instead of Tools
Step-4: Now click on Start. After a few minutes, the IP scanner will show a list of IPs with Port 80 open as shown in the below image.
Step-5: Now copy any of the IP from the list, paste it in your browser’s address bar and hit enter. A window will popup asking for username and password. Since most users do not change the passwords, it should most likely work with the default username and password. For most routers the default username-password pair will be admin-admin or admin-password.
Just enter the username-password as specified above and hit enter. If you are lucky you should gain access to the router settings page where you can modify any of the router settings. The settings page can vary from router to router. A sample router settings page is shown below.
If you do not succeed to gain access, select another IP from the list and repeat the step-5. Atleast 1 out of 5 IPs will have a default password and hence you will surely be able to gain access.
What can an Attacker do by Gaining Access to the Router Settings?
By gaining access to the router settings, it is possible for an attacker to modify any of the router settings which results in the malfunction of the router. As a result the target user’s computer will be disconnected from the Internet. In the worst case the attacker can copy the ISP login details from the router to steal the Internet connection or play any kind of prank with the router settings. So the victim has to reconfigure the router in order to bring it back to action.
The Verdict:
If you are using an ADSL router to connect to the Internet, it is highly recommended that you immediately change your password to prevent any such attacks in the future. Who knows, you may be the next victim of such an attack.
Since the configuration varies from router to router, you need to contact your ISP for details on how to change the password for your model.
Warning!
All the information provided in this post are for educational purposes only. Please do not use this information for illegal purposes.
.
Friday, June 25, 2010
List of all the SQL Injection Strings
One of the major problems with SQL is its poor security issues surrounding is the login and url strings. This tutorial is not going to go into detail on why these string work as all these details have been given in my previous article Top 10 Tricks to exploit SQL Server Systems .
First SEARCH the following Keywords in Google or any Search Engine:
admin\login.asp
login.asp
with these two search string you will have plenty of targets to chose from…choose one that is Vulnerable
INJECTION STRINGS: How to use it?
This is the easiest part…very simple
On the login page just enter something like
user:admin (you dont even have to put this.)
pass:’ or 1=1–
or
user:’ or 1=1–
admin:’ or 1=1–
Some sites will have just a password so
password:’ or 1=1–
In fact I have compiled a combo list with strings like this to use on my chosen targets . There are plenty of strings in the list below. There are many other strings involving for instance UNION table access via reading the error pages table structure thus an attack with this method will reveal eventually admin U\P paths.
The one I am interested in are quick access to targets
PROGRAM
i tried several programs to use with these search strings and upto now only Ares has peformed well with quite a bit of success with a combo list formatted this way. Yesteday I loaded 40 eastern targets with 18 positive hits in a few minutes how long would it take to go through 40 sites cutting and pasting each string
combo example:
admin:’ or a=a–
admin:’ or 1=1–
And so on. You don’t have to be admin and still can do anything you want. The most important part is example:’ or 1=1– this is our basic injection string
Now the only trudge part is finding targets to exploit. So I tend to search say google for login.asp or whatever
inurl:login.asp
index of:/admin/login.asp
like this: index of login.asp
result:
http://www3.google.com/search?hl=en&ie=ISO...G=Google+Search
17,000 possible targets trying various searches spews out plent more
Now using proxy set in my browser I click through interesting targets. Seeing whats what on the site pages if interesting I then cut and paste URL as a possible target. After an hour or so you have a list of sites of potential targets like so
http://www.somesite.com/login.asp
http://www.another.com/admin/login.asp
and so on. In a couple of hours you can build up quite a list because I don’t select all results or spider for log in pages. I then save the list fire up Ares and enter
1) A Proxy list
2) My Target IP list
3) My Combo list
4) Start.
Now I dont want to go into problems with users using Ares..thing is i know it works for me…
Sit back and wait. Any target vulnerable will show up in the hits box. Now when it finds a target it will spew all the strings on that site as vulnerable. You have to go through each one on the site by cutting and pasting the string till you find the right one. But the thing is you know you CAN access the site. Really I need a program that will return the hit with a click on url and ignore false outputs. I am still looking for it. This will saves quite a bit of time going to each site and each string to find its not exploitable.
There you go you should have access to your vulnerable target by now
Another thing you can use the strings in the urls were user=? edit the url to the = part and paste ‘ or 1=1– so it becomes
user=’ or 1=1– just as quick as login process
Combo List
There are lot of other variations of the Injection String which I cannot put on my blog because that is Illegal. If you are interested I can send it to you through Email. Just write in your email address in comment and I will send it to you as early as possible but you need to remain patient it may take 1 or 2 days.
As a result of a lot of requests for the list of SQL Injection String and due to lack of time on our behalf to respond to your Comments we have now decided to give the download link for the list of SQL Injection Strings. Now you just need to Subscribe to our RSS Feed via Email and get the Download link at the bottom of the Confirmation Email. Please don’t Forget to click on the Confirmation Link given in that Email.
First SEARCH the following Keywords in Google or any Search Engine:
admin\login.asp
login.asp
with these two search string you will have plenty of targets to chose from…choose one that is Vulnerable
INJECTION STRINGS: How to use it?
This is the easiest part…very simple
On the login page just enter something like
user:admin (you dont even have to put this.)
pass:’ or 1=1–
or
user:’ or 1=1–
admin:’ or 1=1–
Some sites will have just a password so
password:’ or 1=1–
In fact I have compiled a combo list with strings like this to use on my chosen targets . There are plenty of strings in the list below. There are many other strings involving for instance UNION table access via reading the error pages table structure thus an attack with this method will reveal eventually admin U\P paths.
The one I am interested in are quick access to targets
PROGRAM
i tried several programs to use with these search strings and upto now only Ares has peformed well with quite a bit of success with a combo list formatted this way. Yesteday I loaded 40 eastern targets with 18 positive hits in a few minutes how long would it take to go through 40 sites cutting and pasting each string
combo example:
admin:’ or a=a–
admin:’ or 1=1–
And so on. You don’t have to be admin and still can do anything you want. The most important part is example:’ or 1=1– this is our basic injection string
Now the only trudge part is finding targets to exploit. So I tend to search say google for login.asp or whatever
inurl:login.asp
index of:/admin/login.asp
like this: index of login.asp
result:
http://www3.google.com/search?hl=en&ie=ISO...G=Google+Search
17,000 possible targets trying various searches spews out plent more
Now using proxy set in my browser I click through interesting targets. Seeing whats what on the site pages if interesting I then cut and paste URL as a possible target. After an hour or so you have a list of sites of potential targets like so
http://www.somesite.com/login.asp
http://www.another.com/admin/login.asp
and so on. In a couple of hours you can build up quite a list because I don’t select all results or spider for log in pages. I then save the list fire up Ares and enter
1) A Proxy list
2) My Target IP list
3) My Combo list
4) Start.
Now I dont want to go into problems with users using Ares..thing is i know it works for me…
Sit back and wait. Any target vulnerable will show up in the hits box. Now when it finds a target it will spew all the strings on that site as vulnerable. You have to go through each one on the site by cutting and pasting the string till you find the right one. But the thing is you know you CAN access the site. Really I need a program that will return the hit with a click on url and ignore false outputs. I am still looking for it. This will saves quite a bit of time going to each site and each string to find its not exploitable.
There you go you should have access to your vulnerable target by now
Another thing you can use the strings in the urls were user=? edit the url to the = part and paste ‘ or 1=1– so it becomes
user=’ or 1=1– just as quick as login process
Combo List
There are lot of other variations of the Injection String which I cannot put on my blog because that is Illegal. If you are interested I can send it to you through Email. Just write in your email address in comment and I will send it to you as early as possible but you need to remain patient it may take 1 or 2 days.
As a result of a lot of requests for the list of SQL Injection String and due to lack of time on our behalf to respond to your Comments we have now decided to give the download link for the list of SQL Injection Strings. Now you just need to Subscribe to our RSS Feed via Email and get the Download link at the bottom of the Confirmation Email. Please don’t Forget to click on the Confirmation Link given in that Email.
3 Amazing Firefox Hacks
What good is a browser unless you can tweak it, hack it and bend it to your will? No good at all. The more you can hack it, the better it is. And that means that Firefox must be a great browser as when ever you feel that you know everything about it you come across a bunch of hidden (and some not-so-secret) tips and tricks available that will crank Firefox up and pimp your browser. Make it faster, cooler, more efficient. So today I have come up with 3 amazing firefox tricks you might not be aware of.
1. Save Session For All Tabs Opened In Multiple Firefox Windows
If you are an ardent user of Firefox then you may be aware that when more than one firefox windows are opened up, in that case when you close a firefox window, it does ask me the option to save the session and exit, rather it ask to close all the tabs in that firefox window, but it wont save the tabs in other windows. So this way you could not save the session for multiple tabs opened in multiple firefox windows.
In such a case, there is only one option left to save the session for all the tabs opened in separate firefox windows by terminating firefox through task manager, here is how you do it.
Press Ctrl+Shift+Esc to quickly launch task manager, click the process tab and locate firefox.exe and right click selecting the exe and click End Process Tree.
Next time when you will open firefox it will open all the tabs in all the windows that were previously open.
2. Open & Log In to Multiple Accounts Gmail, Facebook, or Twitter Accounts In FireFox
Firefox extension CookiePie manages Firefox’s cookies—small bits of text stored on your computer that tell a site you’re logged in, for example—in such a way that you can log into the same site multiple times.
How to use it?
Just follow the steps given below:
■Install CookiePie Firefox Extension.
■Create a new tab or use an existing one.
■Open the context menu of the tab (i.e: Press the right mouse button over the tab) and select “Toggle On/Off CookiePie”.
■A cookiepie icon will appear over the tab.
■Go to a site (e.g.: http://www.gmail.com) and login into your account.
■Create another tab.
■Enable CookiePie on that tab too.
■Log in with another account on the same site.
3. Bypass Download Waiting Time On Rapidshare, Megaupload, zShare, Mediafire etc
SkipScreen is a really useful firefox addon for lot of users who download various types of files from the popular file and media sharing sites like Rapidshare, Megaupload, zShare, Mediafire, and more.
Most of these file sharing web sites have a annoying waiting time limit before a free user can start downloading the requested file. So, SkipScreen can be really useful in saving your time wasted seeing the download waiting time as it removes the screen of download waiting time from these media sharing sites.
SkipScreen monitors the pages where you see the download time and will get the content you want before the download waiting time completes.
1. Save Session For All Tabs Opened In Multiple Firefox Windows
If you are an ardent user of Firefox then you may be aware that when more than one firefox windows are opened up, in that case when you close a firefox window, it does ask me the option to save the session and exit, rather it ask to close all the tabs in that firefox window, but it wont save the tabs in other windows. So this way you could not save the session for multiple tabs opened in multiple firefox windows.
In such a case, there is only one option left to save the session for all the tabs opened in separate firefox windows by terminating firefox through task manager, here is how you do it.
Press Ctrl+Shift+Esc to quickly launch task manager, click the process tab and locate firefox.exe and right click selecting the exe and click End Process Tree.
Next time when you will open firefox it will open all the tabs in all the windows that were previously open.
2. Open & Log In to Multiple Accounts Gmail, Facebook, or Twitter Accounts In FireFox
Firefox extension CookiePie manages Firefox’s cookies—small bits of text stored on your computer that tell a site you’re logged in, for example—in such a way that you can log into the same site multiple times.
How to use it?
Just follow the steps given below:
■Install CookiePie Firefox Extension.
■Create a new tab or use an existing one.
■Open the context menu of the tab (i.e: Press the right mouse button over the tab) and select “Toggle On/Off CookiePie”.
■A cookiepie icon will appear over the tab.
■Go to a site (e.g.: http://www.gmail.com) and login into your account.
■Create another tab.
■Enable CookiePie on that tab too.
■Log in with another account on the same site.
3. Bypass Download Waiting Time On Rapidshare, Megaupload, zShare, Mediafire etc
SkipScreen is a really useful firefox addon for lot of users who download various types of files from the popular file and media sharing sites like Rapidshare, Megaupload, zShare, Mediafire, and more.
Most of these file sharing web sites have a annoying waiting time limit before a free user can start downloading the requested file. So, SkipScreen can be really useful in saving your time wasted seeing the download waiting time as it removes the screen of download waiting time from these media sharing sites.
SkipScreen monitors the pages where you see the download time and will get the content you want before the download waiting time completes.
Gmail Account Hacking Tool
A tool that automatically steals IDs of non-encrypted sessions and breaks into Google Mail accounts has been presented at the Defcon hackers’ conference in Las Vegas.
Last week Google introduced a new feature in Gmail that allows users to permanently switch on SSL and use it for every action involving Gmail, and not only, authentication. Users who did not turn it on now have a serious reason to do so as Mike Perry, the reverse engineer from San Francisco who developed the tool is planning to release it in two weeks.
When you log in to Gmail the website sends a cookie (a text file) containing your session ID to the browser. This file makes it possible for the website to know that you are authenticated and keep you logged in for two weeks, unless you manually hit the sign out button. When you hit sign out this cookie is cleared.
Even though when you log in, Gmail forces the authentication over SSL (Secure Socket Layer), you are not secure because it reverts back to a regular unencrypted connection after the authentication is done. According to Google this behavior was chosen because of low-bandwidth users, as SLL connections are slower.
The problem lies with the fact that every time you access anything on Gmail, even an image, your browser also sends your cookie to the website. This makes it possible for an attacker sniffing traffic on the network to insert an image served from http://mail.google.com and force your browser to send the cookie file, thus getting your session ID. Once this happens the attacker can log in to the account without the need of a password. People checking their e-mail from public wireless hotspots are obviously more likely to get attacked than the ones using secure wired networks. Todd Mumford, from the SEO company called SEO Visions Inc, states “This can be a serious problem for Internet Marketers who travel often and use their wireless laptops and Gmal services often and do not always have access to a secure connection”
Perry mentioned that he notified Google about this situation over a year ago and even though eventually it made this option available, he is not happy with the lack of information. “Google did not explain why using this new feature was so important” he said. He continued and explained the implications of not informing the users, “This gives people who routinely log in to Gmail beginning with an https:// session a false sense of security, because they think they’re secure but they’re really not.”
If you are logging in to your Gmail account from different locations and you would like to benefit from this option only when you are using unsecured networks, you can force it by manually typing https://mail.google.com before you log in. This will access the SSL version of Gmail and it will be persistent over your entire session and not only during authentication.
Last week Google introduced a new feature in Gmail that allows users to permanently switch on SSL and use it for every action involving Gmail, and not only, authentication. Users who did not turn it on now have a serious reason to do so as Mike Perry, the reverse engineer from San Francisco who developed the tool is planning to release it in two weeks.
When you log in to Gmail the website sends a cookie (a text file) containing your session ID to the browser. This file makes it possible for the website to know that you are authenticated and keep you logged in for two weeks, unless you manually hit the sign out button. When you hit sign out this cookie is cleared.
Even though when you log in, Gmail forces the authentication over SSL (Secure Socket Layer), you are not secure because it reverts back to a regular unencrypted connection after the authentication is done. According to Google this behavior was chosen because of low-bandwidth users, as SLL connections are slower.
The problem lies with the fact that every time you access anything on Gmail, even an image, your browser also sends your cookie to the website. This makes it possible for an attacker sniffing traffic on the network to insert an image served from http://mail.google.com and force your browser to send the cookie file, thus getting your session ID. Once this happens the attacker can log in to the account without the need of a password. People checking their e-mail from public wireless hotspots are obviously more likely to get attacked than the ones using secure wired networks. Todd Mumford, from the SEO company called SEO Visions Inc, states “This can be a serious problem for Internet Marketers who travel often and use their wireless laptops and Gmal services often and do not always have access to a secure connection”
Perry mentioned that he notified Google about this situation over a year ago and even though eventually it made this option available, he is not happy with the lack of information. “Google did not explain why using this new feature was so important” he said. He continued and explained the implications of not informing the users, “This gives people who routinely log in to Gmail beginning with an https:// session a false sense of security, because they think they’re secure but they’re really not.”
If you are logging in to your Gmail account from different locations and you would like to benefit from this option only when you are using unsecured networks, you can force it by manually typing https://mail.google.com before you log in. This will access the SSL version of Gmail and it will be persistent over your entire session and not only during authentication.
18 Tips to Improve your Apple iPhone Battery life
The iPhone is a great device for performing a wide variety of functions, like sending email, watching a movie, getting directions to a destination, playing games, surfing the internet, or of course, making a phone call. One thing that hampers the iPhone’s ability to be a worry-free productivity device is its the battery life. It can vary widely depending on how you use your iPhone. So here are few Tips that will definately increase your battery life in your iPhone (They are also applicable to your iPod. Not tested on iPad but you may try it).
1.Power-cycling the iPhone: A good place to start out is by power-cycling the iPhone. You can do this by holding down the power button on the top of the iPhone until you see the “Slide to Power Off” screen. Once the iPhone is off, go ahead and push the power button again to turn it on. Use the iPhone as you normally would and see how the battery life is lasting.
2.Drain the battery fully: Go to Settings -> General -> Auto-Lock and set it to Never. This is to wear the battery down. After the battery discharged and it was shut down for a few minutes push the home button to ‘revive’ it. Once the battery sits a moment it can pull some reserve power. Do this repeatedly until the screen displayed an empty battery image and it wouldn’t stay on for more than a second. Now charge it completely. Now your battery is as good as new.
3.Avoiding the Extremes: If you want to enhance your iPhone battery lifespan remember to avoid temperature extremes. Avoid using your iPhone at temperatures higher than 95° F (or 35° C) and in very cold environments. Using the iPhone in very hot conditions can inflict permanent battery damage whereas cold temp usage causes temporary battery performance degradation.
4.Regular Updates: Keep your iPhone software constantly updated to ensure your phone has the latest battery performance maximisation technology.
5.Optimise the Settings: Some apps are battery draining like viewing videos, gaming, email and so on. Just remember the following battery tips to maximise its life.
■Minimize use of Location Services by using it only when needed or disabling the location services option.
■Set your Fetch New Data options to hourly or fetch data manually. Frequent use of mail client only drains the battery faster.
■Disable your Push Mail client when not needed to avoid receiving mail as they arrive.
6.Limit Third-party Application Usage: 3 rd party apps like games prevent auto power saving options like screen dimming or switching off hence the battery is constantly at peak performance.
7.Turn off Wi-Fi, Bluetooth and 3G: When not in use switch off these apps to conserve battery. Also note using Wi-Fi to access the net instead of the cellular network service requires less power.
8.Use your iPhone regularly: It may sound weird but its true that not using the iPhone for long time at a stretch decreases the battery life. Use it regularly and charge the battery at least once every six months even if you don’t use your iPhone regularly.
9.Turn off keyboard clicks: If you frequently use your iPhone’s keyboard, navigate to the Sounds pane of Settings and turn the option for Keyboard clicks off.
10.Connect iPhone directly to computer to charge: If you are connecting your iPhone to a computer instead of a wall socket to charge it, don’t connect iPhone to your keyboard or another USB hub/bridge. Make sure it is plugged directly into one of your computer’s USB 2.0 ports.
11.Turn off 3G: If you’re really low on battery, and are willing to do whatever it takes to keep the phone alive for emergency situations, then go and turn off 3G. Hey, EDGE sucks, but it still works.
12.Turn off EQ: Applying EQ settings to your iPhone apparently drains extra battery. If you’re planning on keeping your phone alive all day, turn the EQ settings off.
13.Turn Off Vibrate in Games: A lot of games have very frequent vibrations, which drain battery life. If you can, turn them off in the game’s settings.
14.Don’t download from iTunes or App Store wirelessly: Downloading apps and media is hard on the battery. Just wait until you get home and use your computer.
15.Turn SSH Off: SSH runs is background and drains battery, this can be turned off from the application BossPrefs OR from default SSH service icon. This runs in the background to detect any network activity and this is the main cause of poor battery time for all jailbreak iPhones.
16.Turn off Auto-Brightness: Auto brightness changes the iPhone’s screen brightness on the basis of surrounding light which consumes battery through auto brightness process and changing from low brightness to high brightness level. Turing off this process will stop a back end process and constant brightness level will not consume more battery due to change in brightness level.
17.Lower the Brightness: More screen brightness requires more battery. A reasonable brightness level is between, 25% to 30% which will brighten up the iPhone screen display good for both day and night.
18.Use your discretion: You understand what’s bad for battery life – doing things that look like they would take a lot of battery life. Just be reasonable. Plan ahead. When you know you won’t charge your phone for hours, don’t go playing games. Resist. Don’t pass your phone around to your friends who say “Oohhh iPhone lemme play.” Don’t take the smart out of smart phone.
1.Power-cycling the iPhone: A good place to start out is by power-cycling the iPhone. You can do this by holding down the power button on the top of the iPhone until you see the “Slide to Power Off” screen. Once the iPhone is off, go ahead and push the power button again to turn it on. Use the iPhone as you normally would and see how the battery life is lasting.
2.Drain the battery fully: Go to Settings -> General -> Auto-Lock and set it to Never. This is to wear the battery down. After the battery discharged and it was shut down for a few minutes push the home button to ‘revive’ it. Once the battery sits a moment it can pull some reserve power. Do this repeatedly until the screen displayed an empty battery image and it wouldn’t stay on for more than a second. Now charge it completely. Now your battery is as good as new.
3.Avoiding the Extremes: If you want to enhance your iPhone battery lifespan remember to avoid temperature extremes. Avoid using your iPhone at temperatures higher than 95° F (or 35° C) and in very cold environments. Using the iPhone in very hot conditions can inflict permanent battery damage whereas cold temp usage causes temporary battery performance degradation.
4.Regular Updates: Keep your iPhone software constantly updated to ensure your phone has the latest battery performance maximisation technology.
5.Optimise the Settings: Some apps are battery draining like viewing videos, gaming, email and so on. Just remember the following battery tips to maximise its life.
■Minimize use of Location Services by using it only when needed or disabling the location services option.
■Set your Fetch New Data options to hourly or fetch data manually. Frequent use of mail client only drains the battery faster.
■Disable your Push Mail client when not needed to avoid receiving mail as they arrive.
6.Limit Third-party Application Usage: 3 rd party apps like games prevent auto power saving options like screen dimming or switching off hence the battery is constantly at peak performance.
7.Turn off Wi-Fi, Bluetooth and 3G: When not in use switch off these apps to conserve battery. Also note using Wi-Fi to access the net instead of the cellular network service requires less power.
8.Use your iPhone regularly: It may sound weird but its true that not using the iPhone for long time at a stretch decreases the battery life. Use it regularly and charge the battery at least once every six months even if you don’t use your iPhone regularly.
9.Turn off keyboard clicks: If you frequently use your iPhone’s keyboard, navigate to the Sounds pane of Settings and turn the option for Keyboard clicks off.
10.Connect iPhone directly to computer to charge: If you are connecting your iPhone to a computer instead of a wall socket to charge it, don’t connect iPhone to your keyboard or another USB hub/bridge. Make sure it is plugged directly into one of your computer’s USB 2.0 ports.
11.Turn off 3G: If you’re really low on battery, and are willing to do whatever it takes to keep the phone alive for emergency situations, then go and turn off 3G. Hey, EDGE sucks, but it still works.
12.Turn off EQ: Applying EQ settings to your iPhone apparently drains extra battery. If you’re planning on keeping your phone alive all day, turn the EQ settings off.
13.Turn Off Vibrate in Games: A lot of games have very frequent vibrations, which drain battery life. If you can, turn them off in the game’s settings.
14.Don’t download from iTunes or App Store wirelessly: Downloading apps and media is hard on the battery. Just wait until you get home and use your computer.
15.Turn SSH Off: SSH runs is background and drains battery, this can be turned off from the application BossPrefs OR from default SSH service icon. This runs in the background to detect any network activity and this is the main cause of poor battery time for all jailbreak iPhones.
16.Turn off Auto-Brightness: Auto brightness changes the iPhone’s screen brightness on the basis of surrounding light which consumes battery through auto brightness process and changing from low brightness to high brightness level. Turing off this process will stop a back end process and constant brightness level will not consume more battery due to change in brightness level.
17.Lower the Brightness: More screen brightness requires more battery. A reasonable brightness level is between, 25% to 30% which will brighten up the iPhone screen display good for both day and night.
18.Use your discretion: You understand what’s bad for battery life – doing things that look like they would take a lot of battery life. Just be reasonable. Plan ahead. When you know you won’t charge your phone for hours, don’t go playing games. Resist. Don’t pass your phone around to your friends who say “Oohhh iPhone lemme play.” Don’t take the smart out of smart phone.
5 Popular Data Backup Freewares
The post consists of programs for making duplicate copies of your computer files, digital photos, music, movies, or anything else on your hard drive or portable device that you’d like to duplicate in case of accident or catastrophe.
1. Paragon Backup & Recovery Free Edition (32 bit)
Back up and restore your Windows system.
Paragon Backup & Recovery 10.2 Free Edition – a disaster recovery tool for stand-alone Windows-based PCs. Combining all the existing backup techniques and exclusive recovery environments, this latest edition satisfies the needs of even the most demanding user and is simply the most powerful free backup tool available today.
Paragon launches 2 versions of Backup & Recovery 10.2. 32-bit provides support for 32-bit systems. And 64-bit for 64-bit Operating Systems. Paragon Backup & Recovery 10.2 Free Edition allows you to take complete control of your PC’s safety. Based on solid commercial backup and recovery software from Paragon, it has a rich set of features that you can trust. Simple to install and easy to use.
2. Macrium Reflect Free
Create, burn, and back up disk images.
Macrium Reflect Free Edition. An award winning disk imaging solution for free. A complete disaster recovery solution for your home and office. Protect your personal documents, photos, music and e-mails. Upgrade your hard disk or try new operating systems in the safe knowledge that everything is securely saved in an easily recovered backup file. Macrium Reflect supports backup to local, network and USB drives as well as burning to all DVD formats. This version is for non-commercial home use.
What’s new in this version:
Version 4.2 build 2733 may include unspecified updates, enhancements, or bug fixes.
3. Easeus Todo Backup
Back up and restore data on your system, partition, or hard disk.
EASEUS Todo Backup is a backup and restore solution for a good reason: with detailed instruction wizards, your computer will be in a safe condition within minutes without the help of an IT specialist to backup your system state, partition and disk. EASEUS Todo Backup can backup your system partition to quickly get the system up and running in the event of a system crash or hardware failure. It allows you to backup and restore disk or partition after viruses attack, unstable software download, hard drive failure. Meanwhile, EASEUS Todo Backup is useful if you want to upgrade the older smaller hard disk without reinstalling the operating system and applications once again.
4. Second Backup Free Edition
Easy-to-use file backup and folder sync tool.
Second Backup is an easy-to-use file backup and sync tool, it can archive multiple versions backed up copies for different time (for example, the first copy for Monday is ‘Backup_1′, the second copy for Tuesday is ‘Backup_2′). Automatically backup your important data (includes opening/using files and folders) to external hard drive, USB disk, network, and other storage device. Intuitive interface makes it easy to use, simply tell it which file or folder to backup, where and when to archive them, then it works reliably in the background and uses very little system resources. The backup task can be directed only copy the new or modified files, it monitors the source files and automatically backups the new or changed file to the destination. Automatic scheduling includes specific days of the week, days of the month, hours of the day, or any desired time intervals. E-mail notification lets you know the file backup status anytime and anywhere.
Note: It says it’s "free" and even has "Free Edition" in it’s name but it’s a 30 day evaluation copy which says after 30 days you must buy it.
5. FBackup
Protect your files/folders from data loss.
FBackup is freeware backup program for Windows. FBackup protects your important files and folders from partial or total loss by automating backup tasks, password protecting and compressing it to save storage space. Using FBackup you can easily backup to any local or network drive or to external drives (such as USB drives). FBackup can backup open/locked files and it can perform full and mirror backups (backup type that does not compress the files).
When defining a backup you can also set file filters and schedule the backup for automatic execution. You can run predefined backups, such as My Documents, My Pictures, or Outlook Express and load backup plug-ins that will back up the settings and data of specific applications. FBackup has ZIP64 support (can create backups over 2GB) and creates standard ZIP files, meaning that you can access it with any zip compatible utility.
1. Paragon Backup & Recovery Free Edition (32 bit)
Back up and restore your Windows system.
Paragon Backup & Recovery 10.2 Free Edition – a disaster recovery tool for stand-alone Windows-based PCs. Combining all the existing backup techniques and exclusive recovery environments, this latest edition satisfies the needs of even the most demanding user and is simply the most powerful free backup tool available today.
Paragon launches 2 versions of Backup & Recovery 10.2. 32-bit provides support for 32-bit systems. And 64-bit for 64-bit Operating Systems. Paragon Backup & Recovery 10.2 Free Edition allows you to take complete control of your PC’s safety. Based on solid commercial backup and recovery software from Paragon, it has a rich set of features that you can trust. Simple to install and easy to use.
2. Macrium Reflect Free
Create, burn, and back up disk images.
Macrium Reflect Free Edition. An award winning disk imaging solution for free. A complete disaster recovery solution for your home and office. Protect your personal documents, photos, music and e-mails. Upgrade your hard disk or try new operating systems in the safe knowledge that everything is securely saved in an easily recovered backup file. Macrium Reflect supports backup to local, network and USB drives as well as burning to all DVD formats. This version is for non-commercial home use.
What’s new in this version:
Version 4.2 build 2733 may include unspecified updates, enhancements, or bug fixes.
3. Easeus Todo Backup
Back up and restore data on your system, partition, or hard disk.
EASEUS Todo Backup is a backup and restore solution for a good reason: with detailed instruction wizards, your computer will be in a safe condition within minutes without the help of an IT specialist to backup your system state, partition and disk. EASEUS Todo Backup can backup your system partition to quickly get the system up and running in the event of a system crash or hardware failure. It allows you to backup and restore disk or partition after viruses attack, unstable software download, hard drive failure. Meanwhile, EASEUS Todo Backup is useful if you want to upgrade the older smaller hard disk without reinstalling the operating system and applications once again.
4. Second Backup Free Edition
Easy-to-use file backup and folder sync tool.
Second Backup is an easy-to-use file backup and sync tool, it can archive multiple versions backed up copies for different time (for example, the first copy for Monday is ‘Backup_1′, the second copy for Tuesday is ‘Backup_2′). Automatically backup your important data (includes opening/using files and folders) to external hard drive, USB disk, network, and other storage device. Intuitive interface makes it easy to use, simply tell it which file or folder to backup, where and when to archive them, then it works reliably in the background and uses very little system resources. The backup task can be directed only copy the new or modified files, it monitors the source files and automatically backups the new or changed file to the destination. Automatic scheduling includes specific days of the week, days of the month, hours of the day, or any desired time intervals. E-mail notification lets you know the file backup status anytime and anywhere.
Note: It says it’s "free" and even has "Free Edition" in it’s name but it’s a 30 day evaluation copy which says after 30 days you must buy it.
5. FBackup
Protect your files/folders from data loss.
FBackup is freeware backup program for Windows. FBackup protects your important files and folders from partial or total loss by automating backup tasks, password protecting and compressing it to save storage space. Using FBackup you can easily backup to any local or network drive or to external drives (such as USB drives). FBackup can backup open/locked files and it can perform full and mirror backups (backup type that does not compress the files).
When defining a backup you can also set file filters and schedule the backup for automatic execution. You can run predefined backups, such as My Documents, My Pictures, or Outlook Express and load backup plug-ins that will back up the settings and data of specific applications. FBackup has ZIP64 support (can create backups over 2GB) and creates standard ZIP files, meaning that you can access it with any zip compatible utility.
Monday, June 21, 2010
How To Shutdown A Computer With A Cell Phone/Email
In this tutorial, I am going to teach you how you can control your computer’s basic function using Microsoft Outlook and your Cell Phone Network. For this tutorial I am demonstrating how a user can shutdown, restart, hibernate their computer, just by sending an email from their phone.
To make this happen, all you need is Microsoft Outlook installed on the PC which you want to control from your cell phone
Now let’s begin with the tutorial.
First, you need the batch files to perform the Shutdown, Hibernate operation.
For example,
shutdown -r -t 10 -c “shutting down”
Copy this code and paste it in notepad, save it as shutdown.bat
Now open up Microsoft Outlook. I am assuming that you have already configured it for your Email and I am not going to teach you about setting mail in Microsoft Outlook. Now we will need to make it so that Outlook checks your inbox about every minute.
You can do this by going to Tools>Options. Then click on Mail Setup tab, and then, the Send/Receive button.
Make sure that the Schedule an automatic send/receive every… box is checked, and set the number of minutes to 1 or anytime you may like. Now you may close all of these dialog boxes.
Now go to Tools>Rules and Alerts. Click on E-mail Rules tab. In new window select Check messages when they arrive and click Next.
Now in next page, check on, on this machine only and with specific words in the subject.
After checking these two values, click on specific words underlined.
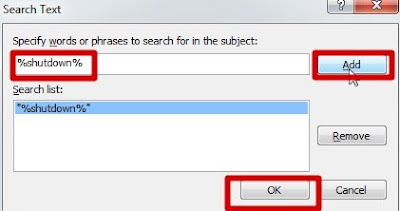
Search Text window will open, in the input field type the command that shuts down the PC. You can use any commands. For prevention of accidental execution I kept %shutdown% as a command. Click on Add button after you are done and click on OK.
Now click on Next.
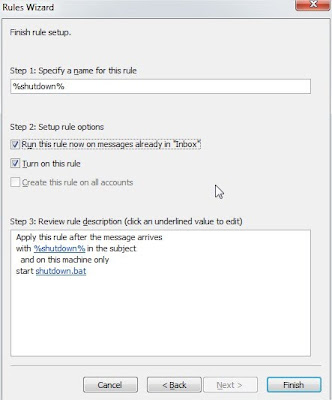
In the next window check mark on start application. In the lower screen, click on application link.
Now you’ll be welcomed to your familiar file open window. Load all files. And select the batch file that you’ve created to shutdown your PC.
If everything went well you’ll see the screen similar to below:
Click on Next, again click on next (don’t choose any things in this step). And finally click on Finish button.
You’ll have %shutdown% alert shown in the E-mail Rules tab.
Now, when you send a message from your phone to your e-mail address with the Subject %shutdown% your computer will trigger shutdown.bat file and instantly executes the command in that batch file finally leading to shutdown the PC.
You can use any batch file to execute any command.
To make this happen, all you need is Microsoft Outlook installed on the PC which you want to control from your cell phone
Now let’s begin with the tutorial.
First, you need the batch files to perform the Shutdown, Hibernate operation.
For example,
shutdown -r -t 10 -c “shutting down”
Copy this code and paste it in notepad, save it as shutdown.bat
Now open up Microsoft Outlook. I am assuming that you have already configured it for your Email and I am not going to teach you about setting mail in Microsoft Outlook. Now we will need to make it so that Outlook checks your inbox about every minute.
You can do this by going to Tools>Options. Then click on Mail Setup tab, and then, the Send/Receive button.
Make sure that the Schedule an automatic send/receive every… box is checked, and set the number of minutes to 1 or anytime you may like. Now you may close all of these dialog boxes.
Now go to Tools>Rules and Alerts. Click on E-mail Rules tab. In new window select Check messages when they arrive and click Next.
Now in next page, check on, on this machine only and with specific words in the subject.
After checking these two values, click on specific words underlined.
Search Text window will open, in the input field type the command that shuts down the PC. You can use any commands. For prevention of accidental execution I kept %shutdown% as a command. Click on Add button after you are done and click on OK.
Now click on Next.
In the next window check mark on start application. In the lower screen, click on application link.
Now you’ll be welcomed to your familiar file open window. Load all files. And select the batch file that you’ve created to shutdown your PC.
If everything went well you’ll see the screen similar to below:
Click on Next, again click on next (don’t choose any things in this step). And finally click on Finish button.
You’ll have %shutdown% alert shown in the E-mail Rules tab.
Now, when you send a message from your phone to your e-mail address with the Subject %shutdown% your computer will trigger shutdown.bat file and instantly executes the command in that batch file finally leading to shutdown the PC.
You can use any batch file to execute any command.
Saturday, June 19, 2010
Take Ownership of Files and Folders in Windows 7 – An Easy Way
If you are a Windows 7 user, then you are most likely be aware of the fact that you need to TAKE OWNERSHIP of files and folders before you can make any changes to them. This feature was introduced in order to prevent any unauthorized changes from being made to the system files. However it can be little annoying to follow a long list of procedure every time you want to take ownership of a certain file or folder. So to make this job simpler, I have found a nice tool called Take Ownership Shell Extension which adds the “Take Ownership” option to the Windows context menu. This makes taking ownership too simple and requires no more than a click.
Just run the portable tool kit and click on the “Install” button. This will add the “Take Ownership” option onto the context menu. To take ownership all you need to do is, just right-click on any of the desired file or folder and click the option “Take Ownership“.
In case if you wish to uninstall this tool at any time, you can just run the tool again and click on the ”Uninstall” button. I hope you like this tool. This works on both Windows 7 and Windows Vista. You can download it from the following link.
Download Take Ownership Shell Extention
Just run the portable tool kit and click on the “Install” button. This will add the “Take Ownership” option onto the context menu. To take ownership all you need to do is, just right-click on any of the desired file or folder and click the option “Take Ownership“.
In case if you wish to uninstall this tool at any time, you can just run the tool again and click on the ”Uninstall” button. I hope you like this tool. This works on both Windows 7 and Windows Vista. You can download it from the following link.
Download Take Ownership Shell Extention
Sunday, June 13, 2010
What is CAPTCHA and How it Works?
CAPTCHA or Captcha (pronounced as cap-ch-uh) which stands for “Completely Automated Public Turing test to tell Computers and Humans Apart” is a type of challenge-response test to ensure that the response is only generated by humans and not by a computer. In simple words, CAPTCHA is the word verification test that you will come across the end of a sign-up form while signing up for Gmail or Yahoo account. The following image shows the typical samples of CAPTCHA.
Almost every Internet user will have an experience of CAPTCHA in their daily Internet usage, but only a few are aware of what it is and why they are used. So in this post you will find a detailed information on how CAPTCHA works and why they are used.
What Purpose does CAPTCHA Exactly Serve?
CAPTCPA is mainly used to prevent automated software (bots) from performing actions on behalf of actual humans. For example while signing up for a new email account, you will come across a CAPTCHA at the end of the sign-up form so as to ensure that the form is filled out only by a legitimate human and not by any of the automated software or a computer bot. The main goal of CAPTCHA is to put forth a test which is simple and straight forward for any human to answer but for a computer, it is almost impossible to solve.
What is the Need to Create a Test that Can Tell Computers and Humans Apart?
For many the CAPTCHA may seem to be silly and annoying, but in fact it has the ability to protect systems from malicious attacks where people try to game the system. Attackers can make use of automated softwares to generate a huge quantity of requests thereby causing a high load on the target server which would degrade the quality of service of a given system, whether due to abuse or resource expenditure. This can affect millions of legitimate users and their requests. CAPTCHAs can be deployed to protect systems that are vulnerable to email spam, such as the services from Gmail, Yahoo and Hotmail.
Who Uses CAPTCHA?
CAPTCHAs are mainly used by websites that offer services like online polls and registration forms. For example, Web-based email services like Gmail, Yahoo and Hotmail offer free email accounts for their users. However upon each sign-up process, CAPTCHAs are used to prevent spammers from using a bot to generate hundreds of spam mail accounts.
Designing a CAPTCHA System
CAPTCHAs are designed on the fact that computers lack the ability that human beings have when it comes to processing visual data. It is more easily possible for humans to look at an image and pick out the patterns than a computer. This is because computers lack the real intelligence that humans have by default. CAPTCHAs are implemented by presenting users with an image which contains distorted or randomly stretched characters which only humans should be able to identify. Sometimes characters are striked out or presented with a noisy background to make it even more harder for computers to figure out the patterns.
Most, but not all, CAPTCHAs rely on a visual test. Some Websites implement a totally different CAPTCHA system to tell humans and computers apart. For example, a user is presented with 4 images in which 3 contains picture of animals and one contain a flower. The user is asked to select only those images which contain animals in them. This Turing test can easily be solved by any human, but almost impossible for a computer.
Breaking the CAPTCHA
The challenge in breaking the CAPTCHA lies in real hard task of teaching a computer how to process information in a way similar to how humans think. Algorithms with artificial intelligence (AI) will have to be designed in order to make the computer think like humans when it comes to recognizing the patterns in images. However there is no universal algorithm that could pass through and break any CAPTCHA system and hence each CAPTCHA algorithm must have to be tackled individually. It might not work 100 percent of the time, but it can work often enough to be worthwhile to spammers.
Almost every Internet user will have an experience of CAPTCHA in their daily Internet usage, but only a few are aware of what it is and why they are used. So in this post you will find a detailed information on how CAPTCHA works and why they are used.
What Purpose does CAPTCHA Exactly Serve?
CAPTCPA is mainly used to prevent automated software (bots) from performing actions on behalf of actual humans. For example while signing up for a new email account, you will come across a CAPTCHA at the end of the sign-up form so as to ensure that the form is filled out only by a legitimate human and not by any of the automated software or a computer bot. The main goal of CAPTCHA is to put forth a test which is simple and straight forward for any human to answer but for a computer, it is almost impossible to solve.
What is the Need to Create a Test that Can Tell Computers and Humans Apart?
For many the CAPTCHA may seem to be silly and annoying, but in fact it has the ability to protect systems from malicious attacks where people try to game the system. Attackers can make use of automated softwares to generate a huge quantity of requests thereby causing a high load on the target server which would degrade the quality of service of a given system, whether due to abuse or resource expenditure. This can affect millions of legitimate users and their requests. CAPTCHAs can be deployed to protect systems that are vulnerable to email spam, such as the services from Gmail, Yahoo and Hotmail.
Who Uses CAPTCHA?
CAPTCHAs are mainly used by websites that offer services like online polls and registration forms. For example, Web-based email services like Gmail, Yahoo and Hotmail offer free email accounts for their users. However upon each sign-up process, CAPTCHAs are used to prevent spammers from using a bot to generate hundreds of spam mail accounts.
Designing a CAPTCHA System
CAPTCHAs are designed on the fact that computers lack the ability that human beings have when it comes to processing visual data. It is more easily possible for humans to look at an image and pick out the patterns than a computer. This is because computers lack the real intelligence that humans have by default. CAPTCHAs are implemented by presenting users with an image which contains distorted or randomly stretched characters which only humans should be able to identify. Sometimes characters are striked out or presented with a noisy background to make it even more harder for computers to figure out the patterns.
Most, but not all, CAPTCHAs rely on a visual test. Some Websites implement a totally different CAPTCHA system to tell humans and computers apart. For example, a user is presented with 4 images in which 3 contains picture of animals and one contain a flower. The user is asked to select only those images which contain animals in them. This Turing test can easily be solved by any human, but almost impossible for a computer.
Breaking the CAPTCHA
The challenge in breaking the CAPTCHA lies in real hard task of teaching a computer how to process information in a way similar to how humans think. Algorithms with artificial intelligence (AI) will have to be designed in order to make the computer think like humans when it comes to recognizing the patterns in images. However there is no universal algorithm that could pass through and break any CAPTCHA system and hence each CAPTCHA algorithm must have to be tackled individually. It might not work 100 percent of the time, but it can work often enough to be worthwhile to spammers.